Question 37
- (Topic 7)
Exhibit: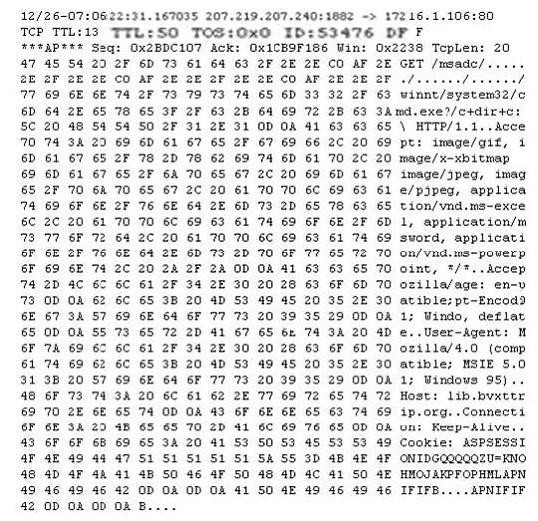
Study the following log extract and identify the attack.
Correct Answer:D
The “Get /msadc/……/……/……/winnt/system32/cmd.exe?” shows that a Unicode Directory Traversal Attack has been performed.
Question 38
- (Topic 7)
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
Correct Answer:C
-N = NON interactive mode (without ncurses)
-C = collect all users and passwords
-L = if used with -C (collector) it creates a file with all the password sniffed in the session in the form "YYYYMMDD-collected-pass.log"
-z = start in silent mode (no arp storm on start up)
-s = IP BASED sniffing
--quiet = "demonize" ettercap. Useful if you want to log all data in background.
Question 39
- (Topic 1)
Neil is a network administrator working in Istanbul. Neil wants to setup a protocol analyzer on his network that will receive a copy of every packet that passes through the main office switch. What type of port will Neil need to setup in order to accomplish this?
Correct Answer:B
Question 40
- (Topic 6)
What are two things that are possible when scanning UDP ports? (Choose two.
Correct Answer:BE
Closed UDP ports can return an ICMP type 3 code 3 message. No response can mean the port is open or the packet was silently dropped.
Question 41
- (Topic 6)
Because UDP is a connectionless protocol: (Select 2)
Correct Answer:DE
Neither UDP packets, nor the ICMP errors are guaranteed to arrive, so UDP scanners must also implement retransmission of packets that appear to be lost (or you will get a bunch of false positives).
Question 42
- (Topic 7)
The follows is an email header. What address is that of the true originator of the message?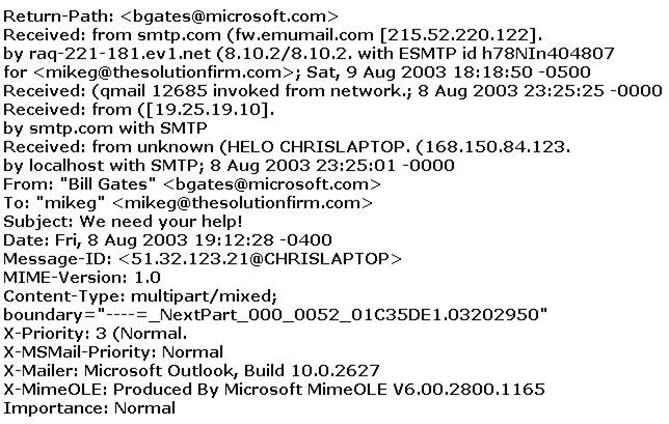
Correct Answer:C
Spoofing can be easily achieved by manipulating the "from" name field, however, it is much more difficult to hide the true source address. The "received from" IP address 168.150.84.123 is the true source of the