Question 13
- (Topic 8)
Exhibit: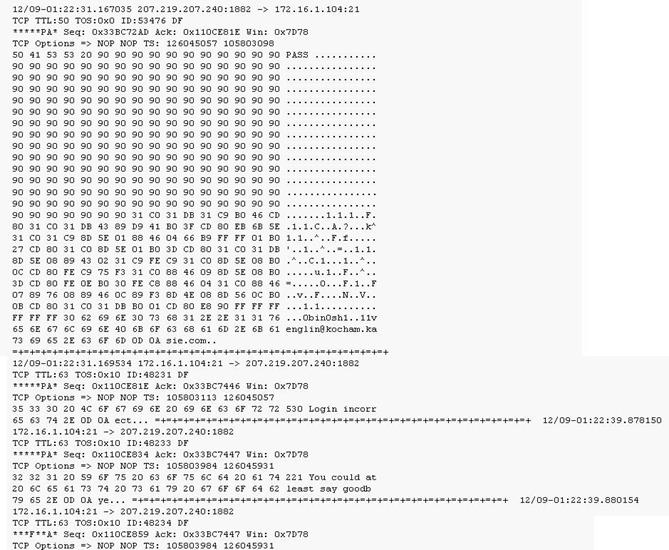
Given the following extract from the snort log on a honeypot, what do you infer from the attack?
Correct Answer:D
The attacker submits a PASS to the honeypot and receives a login incorrect before disconnecting.
Question 14
- (Topic 8)
Which of the following statements best describes the term Vulnerability?
Correct Answer:A
Vulnerabilities are all weaknesses that can be exploited.
Question 15
- (Topic 6)
Study the log below and identify the scan type.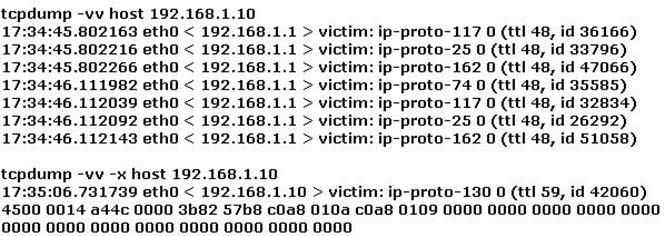
Correct Answer:D
Question 16
- (Topic 7)
What is GINA?
Correct Answer:D
In computing, GINA refers to the graphical identification and authentication library, a component of some Microsoft Windows operating systems that provides secure authentication and interactive logon services.
Question 17
- (Topic 3)
Least privilege is a security concept that requires that a user is
Correct Answer:A
Question 18
- (Topic 7)
You are a Administrator of Windows server. You want to find the port number for POP3. What file would you find the information in and where?
Select the best answer.
Correct Answer:C
Explanations: %windir%\\system32\\drivers\\etc\\services is the correct place to look for this information.