Question 133
- (Topic 2)
How do you defend against MAC attacks on a switch?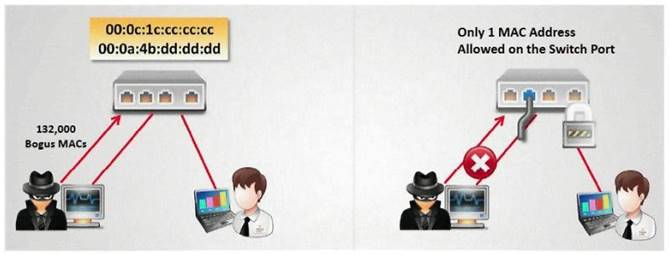
Correct Answer:D
Question 134
- (Topic 8)
What do you conclude from the nmap results below? Staring nmap V. 3.10ALPHA0 (www.insecure.org/map/)
(The 1592 ports scanned but not shown below are in state: closed)
Port State Service 21/tcp open ftp 25/tcp open smtp 80/tcp open http 443/tcp open https
Remote operating system guess: Too many signatures match the reliability guess the OS. Nmap run completed – 1 IP address (1 host up) scanned in 91.66 seconds
Correct Answer:B
There is no reports of any ports being filtered.
Question 135
- (Topic 8)
You have been called to investigate a sudden increase in network traffic at XYZ. It seems that the traffic generated was too heavy that normal business functions could no longer be rendered to external employees and clients. After a quick investigation, you find that the computer has services running attached to TFN2k and Trinoo software. What do you think was the most likely cause behind this sudden increase in traffic?
Correct Answer:A
In computer security, a denial-of-service attack (DoS attack) is an attempt to make a computer resource unavailable to its intended users. Typically the targets are high- profile web servers, and the attack attempts to make the hosted web pages unavailable on the Internet. It is a computer crime that violates the Internet proper use policy as indicated by the Internet Architecture Board (IAB). TFN2K and Trinoo are tools used for conducting DDos attacks.
Question 136
- (Topic 2)
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company's network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place. Your peer, Peter Smith who works at the same department disagrees with you. He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of "weakest link" in the security chain. What is Peter Smith talking about?
Correct Answer:A