Question 73
- (Topic 2)
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server in your organization. They notice that there is excessive number of functions in the source code that might lead to buffer overflow. These C++ functions do not check bounds. Identify the line in the source code that might lead to buffer overflow?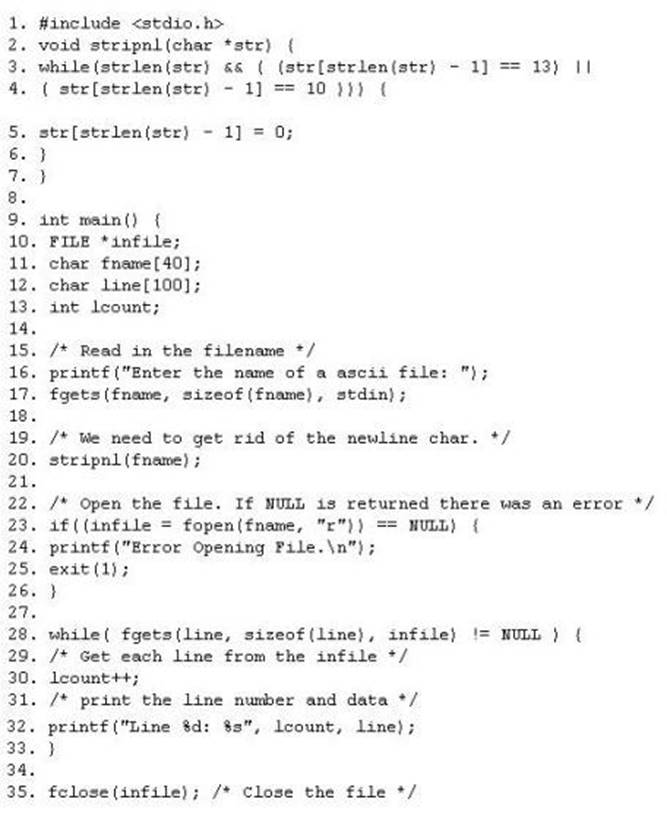
Correct Answer:B
Question 74
- (Topic 2)
LAN Manager Passwords are concatenated to 14 bytes, and split in half. The two halves are hashed individually. If the password is 7 characters or less, than the second half of the hash is always:
Correct Answer:A
Question 75
- (Topic 4)
The intrusion detection system at a software development company suddenly generates multiple alerts regarding attacks against the company's external webserver, VPN concentrator, and DNS servers. What should the security team do to determine which alerts to check first?
Correct Answer:C
Question 76
- (Topic 3)
In the software security development life cyle process, threat modeling occurs in which phase?
Correct Answer:A
Question 77
- (Topic 7)
Global deployment of RFC 2827 would help mitigate what classification of attack?
Correct Answer:C
RFC 2827 - Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing
Question 78
- (Topic 5)
When analyzing the IDS logs, the system administrator notices connections from outside of the LAN have been sending packets where the Source IP address and Destination IP address are the same. There have been no alerts sent via email or logged in the IDS. Which type of an alert is this?
Correct Answer:B