Question 61
- (Topic 4)
Which command line switch would be used in NMAP to perform operating system detection?
Correct Answer:D
Question 62
- (Topic 7)
E-mail scams and mail fraud are regulated by which of the following?
Correct Answer:A
http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001030---- 000-.html
Question 63
- (Topic 4)
A security consultant decides to use multiple layers of anti-virus defense, such as end user desktop anti-virus and E-mail gateway. This approach can be used to mitigate which kind of attack?
Correct Answer:C
Question 64
- (Topic 3)
Which of the following items of a computer system will an anti-virus program scan for viruses?
Correct Answer:A
Question 65
- (Topic 2)
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below: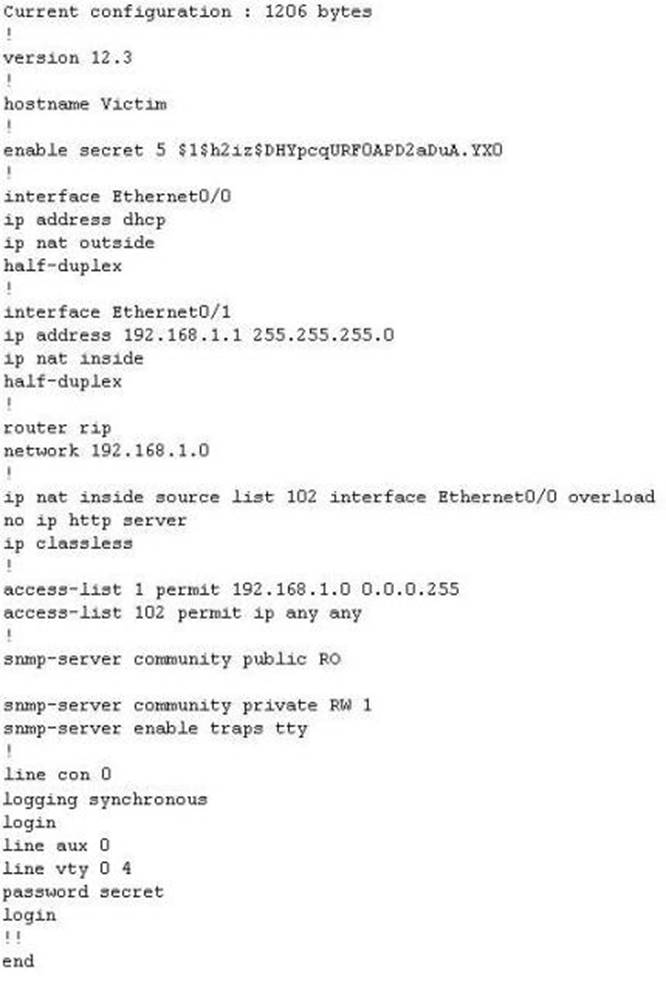
You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
Correct Answer:BD
Question 66
- (Topic 2)
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
Correct Answer:D