Online CEH-001 Practice TestMore GAQM Products >
Free GAQM CEH-001 Exam Dumps Questions
GAQM CEH-001: Certified Ethical Hacker (CEH)
- Get instant access to CEH-001 practice exam questions
- Get ready to pass the Certified Ethical Hacker (CEH) exam right now using our GAQM CEH-001 exam package, which includes GAQM CEH-001 practice test plus an GAQM CEH-001 Exam Simulator.
- The best online CEH-001 exam study material and preparation tool is here.
Question 1
- (Topic 3)
How do you defend against ARP Poisoning attack? (Select 2 answers)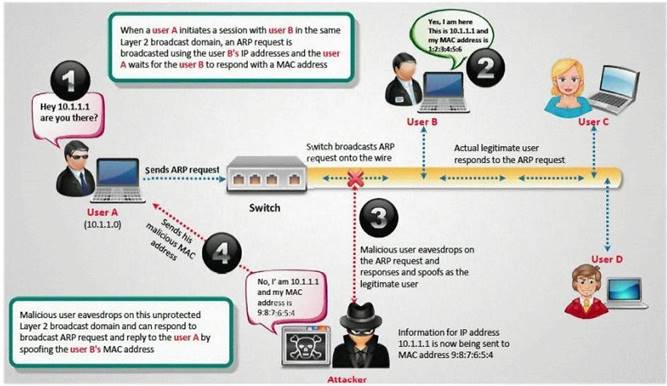
Correct Answer:AC
Question 2
- (Topic 8)
_____ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.
Correct Answer:A
In computer security, mandatory access control (MAC) is a kind of access control, defined by the TCSEC as "a means of restricting access to objects based on the sensitivity (as represented by a label) of the information contained in the objects and the formal authorization (i.e., clearance) of subjects to access information of such sensitivity."
Question 3
- (Topic 2)
_____ is a type of symmetric-key encryption algorithm that transforms a fixed- length block of plaintext (unencrypted text) data into a block of ciphertext (encrypted text) data of the same length.
Correct Answer:B
Question 4
- (Topic 1)
Which of the following statements would NOT be a proper definition for a Trojan Horse?
Correct Answer:A
Question 5
- (Topic 7)
Tess King is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc) for a Domain. What do you think Tess King is trying to accomplish? Select the best answer.
Correct Answer:B
The zone transfer is the method a secondary DNS server uses to update its information from the primary DNS server. DNS servers within a domain are organized using a master-slave method where the slaves get updated DNS information from the master DNS. One should configure the master DNS server to allow zone transfers only from secondary (slave) DNS servers but this is often not implemented. By connecting to a specific DNS server and successfully issuing the ls –d domain-name > file-name you have initiated a zone transfer.
Question 6
- (Topic 5)
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106: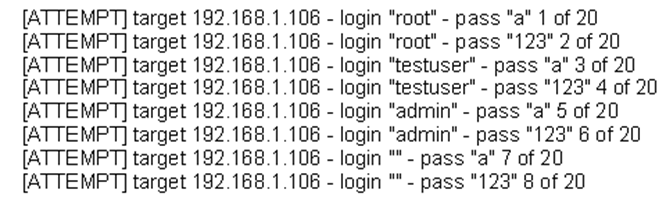
What is most likely taking place?
Correct Answer:B