Question 7
A Cisco PoE switch is shown in the following image. Which type of port will provide both data connectivity and power to an IP phone?
Correct Answer:C
In the provided image of the Cisco PoE switch, the ports identified with number 6 are the standard RJ-45 Ethernet ports typically found on switches that provide both data connectivity and Power over Ethernet (PoE). PoE ports are designed to supply power to devices such as IP phones, wireless access points, and other PoE-enabled devices directly through the Ethernet cable.
Ports:
•2: Console port (for management and configuration)
•3 and 4: Specific function ports (often for management)
•6: RJ-45 Ethernet ports (capable of providing PoE)
•7: SFP ports (for fiber connections, typically do not provide PoE) Thus, the correct answer is C. Ports identified with number 6. References :=
•Cisco Catalyst 2960-L Series Switches Data Sheet
•Cisco PoE Overview
Question 8
DRAG DROP
Move the MFA factors from the list on the left to their correct examples on the right. You may use each factor once, more than once, or not at all.
Note: You will receive partial credit for each correct selection.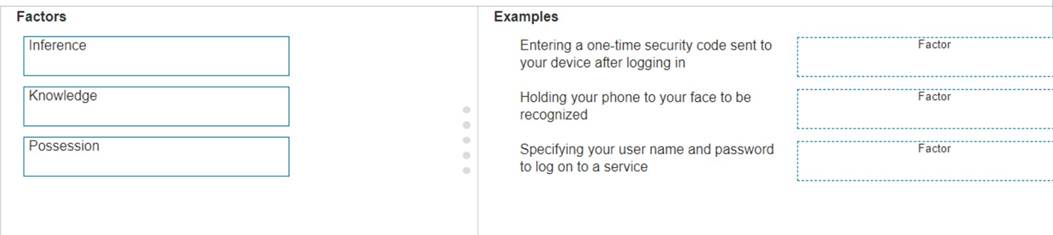
Solution:
The correct matching of the MFA factors to their examples is as follows:
✑ Entering a one-time security code sent to your device after logging in: Possession
✑ Holding your phone to your face to be recognized: Inherence
✑ Specifying your user name and password to log on to a service: Knowledge Here??s why each factor matches the example:
✑ Possession: This factor is something the user has, like a mobile device. A one-
time security code sent to this device falls under this category.
✑ Inherence: This factor is something the user is, such as a biometric characteristic.
Facial recognition using a phone is an example of this factor.
✑ Knowledge: This factor is something the user knows, like a password or PIN. Multi-Factor Authentication (MFA) enhances security by requiring two or more of these factors to verify a user??s identity before granting access.
✑ Entering a one-time security code sent to your device after logging in.
✑ Holding your phone to your face to be recognized.
✑ Specifying your username and password to log on to a service.
✑ Possession Factor: This involves something the user has in their possession.
Receiving a one-time security code on a device (e.g., phone) is an example of this.
✑ Inference Factor (Inherence/Biometric): This involves something inherent to the user, such as biometric verification (e.g., facial recognition or fingerprint scanning).
✑ Knowledge Factor: This involves something the user knows, such as login credentials (username and password).
References:
✑ Multi-Factor Authentication (MFA) Explained: MFA Guide
✑ Understanding Authentication Factors: Authentication Factors
Does this meet the goal?
Correct Answer:A
Question 9
Which information is included in the header of a UDP segment?
Correct Answer:C
The header of a UDP (User Datagram Protocol) segment includesport numbers. Specifically, it contains the source port number and the destination port number, which are used to identify the sending and receiving applications. UDP headers do not include IP addresses or MAC addresses, as those are part of the IP and Ethernet frame headers, respectively.Additionally, UDP does not use sequence numbers, which are a feature of TCP (Transmission Control Protocol) for ensuring reliable delivery of data segments1.
References:=
✑ Segmentation Explained with TCP and UDP Header
✑ User Datagram Protocol (UDP) - GeeksforGeeks
✑ Which three fields are used in a UDP segment header
=========================
✑ UDP Header: The header of a UDP segment includes the following key fields:
✑ IP Addresses: These are included in the IP header, not the UDP header.
✑ Sequence Numbers: These are part of the TCP header, not UDP.
✑ MAC Addresses: These are part of the Ethernet frame header and are not included in the UDP header.
References:
✑ RFC 768 - User Datagram Protocol: RFC 768
✑ Cisco Guide on UDP: Cisco UDP Guide
Question 10
DRAG DROP
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.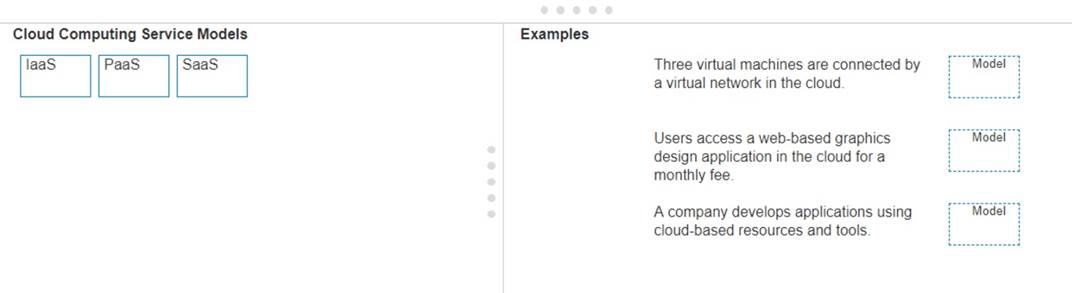
Solution:
✑ Three virtual machines are connected by a virtual network in the cloud.
✑ Users access a web-based graphics design application in the cloud for a monthly fee.
✑ A company develops applications using cloud-based resources and tools.
✑ IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
✑ PaaS (Platform as a Service): Offers a platform with tools and services to develop,
test, and deploy applications.
✑ SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
✑ Cloud Service Models: Understanding IaaS, PaaS, SaaS
✑ NIST Definition of Cloud Computing:NIST Cloud Computing
Does this meet the goal?
Correct Answer:A
Question 11
Which device protects the network by permitting or denying traffic based on IP address, port number, or application?
Correct Answer:A
✑ Firewall: A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It permits or denies traffic based on IP addresses, port numbers, or applications.
✑ Access Point: This is a device that allows wireless devices to connect to a wired
network using Wi-Fi. It does not perform traffic filtering based on IP, port, or application.
✑ VPN Gateway: This device allows for secure connections between networks over
the internet, but it is not primarily used for traffic filtering based on IP, port, or application.
✑ Intrusion Detection System (IDS): This device monitors network traffic for
suspicious activity and policy violations, but it does not actively permit or deny traffic.
References:
✑ Understanding Firewalls: Firewall Basics
Question 12
Which command will display the following output?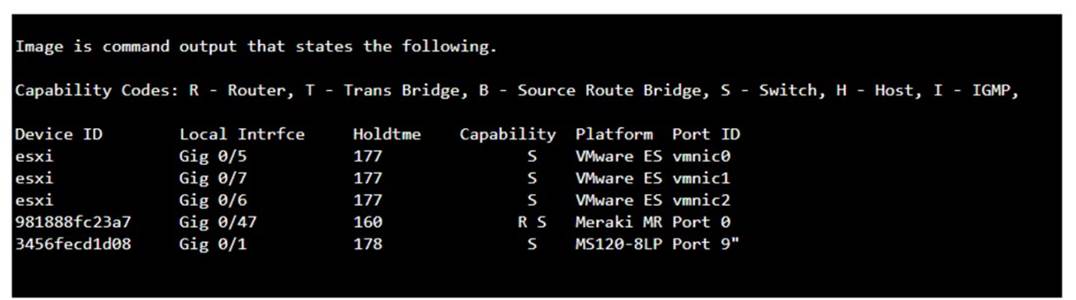
Correct Answer:B
The command that will display the output provided, which includes capability codes, local interface details, device IDs, hold times, and platform port ID capabilities, is the show cdp neighbor command. This command is used in Cisco devices to display current information about neighboring devices detected by Cisco Discovery Protocol (CDP), which includes details such as the interface through which the neighbor is connected, the type of device, and the port ID of the device1.
References :=
•Cisco - show cdp neighbors
The provided output is from the Cisco Discovery Protocol (CDP) neighbor table. The show cdp neighbor command displays information about directly connected Cisco devices, including Device ID, Local Interface, Holdtime, Capability, Platform, and Port ID.
•A. show mac-address-table: Displays the MAC address table on the switch.
•C. show inventory: Displays information about the hardware inventory of the device.
•D. show ip interface: Displays IP interface status and configuration. Thus, the correct answer is B. show cdp neighbor.
References :=
•Cisco CDP Neighbor Command
•Understanding CDP