Online CAS-005 Practice TestMore CompTIA Products >
Free CompTIA CAS-005 Exam Dumps Questions
CompTIA CAS-005: CompTIA SecurityX Exam
- Get instant access to CAS-005 practice exam questions
- Get ready to pass the CompTIA SecurityX Exam exam right now using our CompTIA CAS-005 exam package, which includes CompTIA CAS-005 practice test plus an CompTIA CAS-005 Exam Simulator.
- The best online CAS-005 exam study material and preparation tool is here.
Question 1
A company receives reports about misconfigurations and vulnerabilities in a third-party hardware device that is part of its released products. Which of the following solutions is the best way for the company to identify possible issues at an earlier stage?
Correct Answer:D
Addressing misconfigurations and vulnerabilities in third-party hardware requires a comprehensive approach to manage risks throughout the supply chain. Implementing a proper supply chain risk management (SCRM) program is the most effective solution as it encompasses the following:
✑ Holistic Approach: SCRM considers the entire lifecycle of the product, from initial
design through to delivery and deployment. This ensures that risks are identified and managed at every stage.
✑ Vendor Management: It includes thorough vetting of suppliers and ongoing
assessments of their security practices, which can identify and mitigate vulnerabilities early.
✑ Regular Audits and Assessments: A robust SCRM program involves regular audits
and assessments, both internally and with suppliers, to ensure compliance with security standards and best practices.
✑ Collaboration and Communication: Ensures that there is effective communication
and collaboration between the company and its suppliers, leading to faster identification and resolution of issues.
Other options, while beneficial, do not provide the same comprehensive risk management:
✑ A. Performing vulnerability tests on each device delivered by the providers: While useful, this is reactive and only addresses issues after they have been delivered.
✑ B. Performing regular red-team exercises on the vendor production line: This can identify vulnerabilities but is not as comprehensive as a full SCRM program.
✑ C. Implementing a monitoring process for the integration between the application and the vendor appliance: This is important but only covers the integration phase, not the entire supply chain.
References:
✑ CompTIA SecurityX Study Guide
✑ NIST Special Publication 800-161, "Supply Chain Risk Management Practices for Federal Information Systems and Organizations"
✑ ISO/IEC 27036-1:2014, "Information technology — Security techniques — Information security for supplier relationships"
Question 2
An organization wants to implement a platform to better identify which specific assets are affected by a given vulnerability. Which of the following components provides the best foundation to achieve this goal?
Correct Answer:B
A Configuration Management Database (CMDB) provides the best foundation for identifying which specific assets are affected by a given vulnerability. A CMDB maintains detailed information about the IT environment, including hardware, software, configurations, and relationships between assets. This comprehensive view allows organizations to quickly identify and address vulnerabilities affecting specific assets. References:
✑ CompTIA SecurityX Study Guide: Discusses the role of CMDBs in asset management and vulnerability identification.
✑ ITIL (Information Technology Infrastructure Library) Framework: Recommends the
use of CMDBs for effective configuration and asset management.
✑ "Configuration Management Best Practices" by Bob Aiello and Leslie Sachs: Covers the importance of CMDBs in managing IT assets and addressing vulnerabilities.
Question 3
Which of the following AI concerns is most adequately addressed by input sanitation?
Correct Answer:B
Input sanitation is a critical process in cybersecurity that involves validating and cleaning data provided by users to prevent malicious inputs from causing harm. In the context of AI concerns:
✑ A. Model inversion involves an attacker inferring sensitive data from model
outputs, typically requiring sophisticated methods beyond just manipulating input data.
✑ B. Prompt Injection is a form of attack where an adversary provides malicious input
to manipulate the behavior of AI models, particularly those dealing with natural language processing (NLP). Input sanitation directly addresses this by ensuring that inputs are cleaned and validated to remove potentially harmful commands or instructions that could alter the AI's behavior.
✑ C. Data poisoning involves injecting malicious data into the training set to
compromise the model. While input sanitation can help by filtering out bad data, data poisoning is typically addressed through robust data validation and monitoring during the model training phase, rather than real-time input sanitation.
✑ D. Non-explainable model refers to the lack of transparency in how AI models
make decisions. This concern is not addressed by input sanitation, as it relates more to model design and interpretability techniques.
Input sanitation is most relevant and effective for preventing Prompt Injection attacks, where the integrity of user inputs directly impacts the performance and security of AI models.
References:
✑ CompTIA Security+ Study Guide
✑ "Security of Machine Learning" by Battista Biggio, Blaine Nelson, and Pavel Laskov
✑ OWASP (Open Web Application Security Project) guidelines on input validation and injection attacks
Top of Form Bottom of Form
Question 4
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function: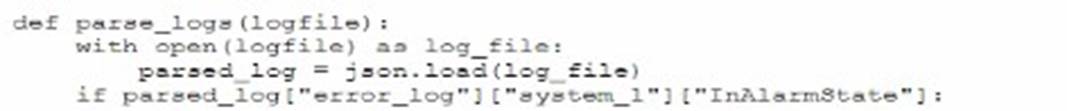
Which of the following is most likely the log input that the code will parse?
A)
B)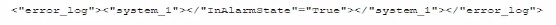
C)
D)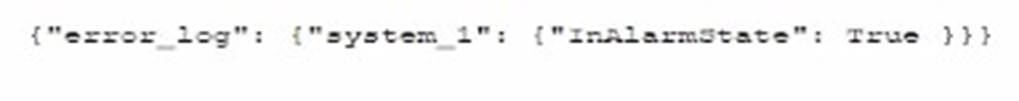
Correct Answer:A
The code function provided in the question seems to be designed to parse JSON formatted logs to check for an alarm state. Option A is a JSON format that matches the structure likely expected by the code. The presence of the "error_log" and "InAlarmState" keys suggests that this is the correct input format.
Reference: CompTIA SecurityX Study Guide, Chapter on Log Management and Automation, Section on Parsing Structured Logs.
Question 5
The material finding from a recent compliance audit indicate a company has an issue with excessive permissions. The findings show that employees changing roles or departments results in privilege creep. Which of the following solutions are the best ways to mitigate this issue? (Select two).
Setting different access controls defined by business area
Correct Answer:AD
To mitigate the issue of excessive permissions and privilege creep, the best solutions are:
✑ Implementing a Role-Based Access Policy:
✑ Performing Periodic Access Reviews:
Question 6
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate. Which of the following is the best way to meet this objective?
Correct Answer:A
The best way to automate reporting from disparate security appliances that do not currently communicate is to configure an API Integration to aggregate the different data sets. Here's why:
✑ Interoperability: APIs allow different systems to communicate and share data, even
if they were not originally designed to work together. This enables the integration of various security appliances into a unified reporting system.
✑ Automation: API integrations can automate the process of data collection,
aggregation, and reporting, reducing manual effort and increasing efficiency.
✑ Scalability: APIs provide a scalable solution that can easily be extended to include
additional security appliances or data sources as needed.
✑ References: