Question 7
A security engineer was auditing an organization’s current software development practice and discovered that multiple opensource libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
Correct Answer:B
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-best-practices/
Question 8
A company publishes several APIs for customers and is required to use keys to segregate customer data sets. Which of the following would be BEST to use to store customer keys?
Correct Answer:C
Reference: https://developer.android.com/studio/publish/app-signing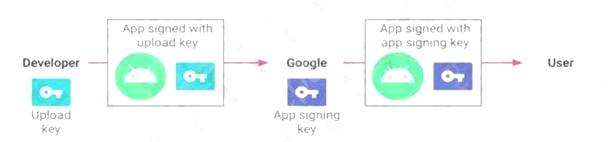
Question 9
A developer is creating a new mobile application for a company. The application uses REST API and TLS 1.2 to communicate securely with the external back- end server. Due to this configuration, the company is concerned about HTTPS interception attacks.
Which of the following would be the BEST solution against this type of attack?
Correct Answer:C
Reference: https://cloud.google.com/security/encryption-in-transit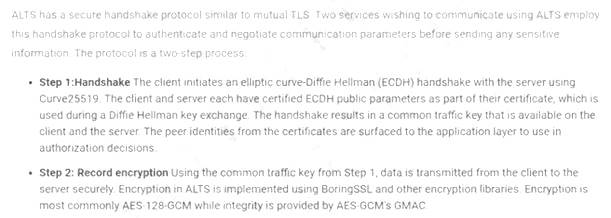
Question 10
A systems administrator is in the process of hardening the host systems before connecting to the network. The administrator wants to add protection to the boot loader to ensure the hosts are secure before the OS fully boots.
Which of the following would provide the BEST boot loader protection?
Correct Answer:D
Reference: https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.security.doc/GUID-898217D4-689D-4EB5-866C-888353FE241C.html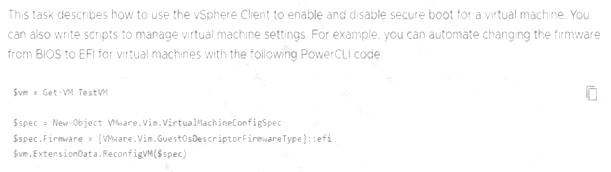
Question 11
A security analyst is investigating a possible buffer overflow attack. The following output was found on a user’s workstation: graphic.linux_randomization.prg Which of the following technologies would mitigate the manipulation of memory segments?
Correct Answer:B
Reference: http://webpages.eng.wayne.edu/~fy8421/19sp-csc5290/labs/lab2-instruction.pdf (3)
Question 12
A security analyst is performing a vulnerability assessment on behalf of a client. The analyst must define what constitutes a risk to the organization. Which of the following should be the analyst’s FIRST action?
Correct Answer:C