Online CAS-004 Practice TestMore CompTIA Products >
Free CompTIA CAS-004 Exam Dumps Questions
CompTIA CAS-004: CompTIA Advanced Security Practitioner (CASP+) Exam
- Get instant access to CAS-004 practice exam questions
- Get ready to pass the CompTIA Advanced Security Practitioner (CASP+) Exam exam right now using our CompTIA CAS-004 exam package, which includes CompTIA CAS-004 practice test plus an CompTIA CAS-004 Exam Simulator.
- The best online CAS-004 exam study material and preparation tool is here.
Question 1
Which of the following is the MOST important security objective when applying cryptography to control messages that tell an ICS how much electrical power to output?
Correct Answer:D
Question 2
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company’s availability requirements. During a postmortem analysis, the following issues were highlighted:
* 1. International users reported latency when images on the web page were initially loading.
* 2. During times of report processing, users reported issues with inventory when attempting to place orders.
* 3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
Correct Answer:A
Question 3
A high-severity vulnerability was found on a web application and introduced to the enterprise. The vulnerability could allow an unauthorized user to utilize an open-source library to view privileged user information. The enterprise is unwilling to accept the risk, but the developers cannot fix the issue right away. Which of the following should be implemented to reduce the risk to an acceptable level until the issue can be fixed?
Correct Answer:D
Reference: https://www.microfocus.com/en-us/what-is/sast
Question 4
An organization’s hunt team thinks a persistent threats exists and already has a foothold in the enterprise network.
Which of the following techniques would be BEST for the hunt team to use to entice the adversary to uncover malicious activity?
Correct Answer:C
Reference: https://www.cynet.com/network-attacks/network-attacks-and-network-security-threats/
Question 5
A shipping company that is trying to eliminate entire classes of threats is developing an SELinux policy to ensure its custom Android devices are used exclusively for package tracking.
After compiling and implementing the policy, in which of the following modes must the company ensure the devices are configured to run?
Correct Answer:B
Reference: https://source.android.com/security/selinux/customize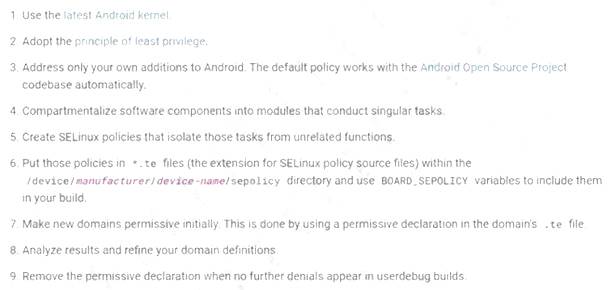
Question 6
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
Correct Answer:B
Reference: https://dzone.com/articles/what-is-oval-a-community-driven-vulnerability-mana