Question 43
Company policy requires that all company laptops meet the following baseline requirements: Software requirements:
Antivirus
Anti-malware Anti-spyware Log monitoring
Full-disk encryption
Terminal services enabled for RDP Administrative access for local users Hardware restrictions:
Bluetooth disabled FireWire disabled WiFi adapter disabled
Ann, a web developer, reports performance issues with her laptop and is not able to access any network resources. After further investigation, a bootkit was discovered and it was trying to access external websites. Which of the following hardening techniques should be applied to mitigate this specific issue from reoccurring? (Select TWO).
Correct Answer:DG
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or areas of its software that would not otherwise be allowed (for example, to an unauthorized user) while at the same time masking its existence or the existence of other software. A bootkit is similar to a rootkit except the malware infects the master boot record on a hard disk. Malicious software such as bootkits or rootkits typically require administrative privileges to be installed.
Therefore, one method of preventing such attacks is to remove administrative access for local users. A common source of malware infections is portable USB flash drives. The flash drives are often plugged into less secure computers such as a user’s home computer and then taken to work and plugged in to a work computer. We can prevent this from happening by restricting or disabling access to USB devices.
Incorrect Answers:
A: Using a group policy to limit web access is not a practical solution. Users in a company often require Web access so restricting it will affect their ability to do their jobs.
B: Rootkits or Bootkits would not be caught by connecting to the network over a VPN so disabling VPN access will not help.
C: Removing full-disk encryption will not prevent Bootkits.
E: Bootkits are not caught by connecting to network resources using Telnet connection so disabling Telnet access to resources will not help.
F: Performing vulnerability scanning on a daily basis might help you to quickly detect Bootkits. However, vulnerability scanning does nothing to actually prevent the Bootkits.
References: https://en.wikipedia.org/wiki/Rootkit
Question 44
Given the following output from a local PC: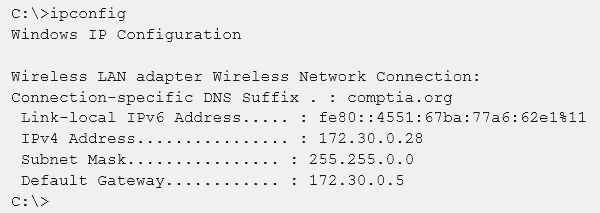
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Correct Answer:B
Question 45
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network.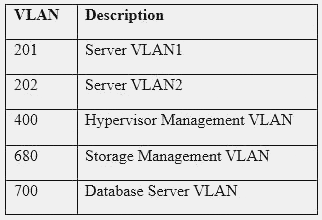
Using the above information, on which VLANs should multicast be enabled?
Correct Answer:D
Question 46
A small retail company recently deployed a new point of sale (POS) system to all 67 stores. The core
of the POS is an extranet site, accessible only from retail stores and the corporate office over a splittunnel VPN. An additional split-tunnel VPN provides bi-directional connectivity back to the main
office, which provides voice connectivity for store VoIP phones. Each store offers guest wireless functionality, as well as employee wireless. Only the staff wireless network has access to the POS VPN. Recently, stores are reporting poor response times when accessing the POS application from store computers as well as degraded voice quality when making phone calls. Upon investigation, it is determined that three store PCs are hosting malware, which is generating excessive network traffic. After malware removal, the information security department is asked to review the configuration
and suggest changes to prevent this from happening again. Which of the following denotes the BEST way to mitigate future malware risk?
Correct Answer:A
A perimeter firewall is located between the local network and the Internet where it can screen network traffic flowing in and out of the organization. A firewall with unified threat management (UTM) functionalities includes anti-malware capabilities.
Incorrect Answers:
B: Antivirus applications prevent viruses, worms and Trojans but not other types of malware, such as spyware.
C: A virtual desktop infrastructure (VDI) solution refers to computer virtualization. It uses servers to provide desktop operating systems to a host machines. This reduces on-site support and improves centralized management. It does not mitigate against malware attacks.
D: Content filtering is used to control the types of email messages that flow in and out of an organization, and the types of web pages a user may access. It does not mitigate against malware attacks.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 92, 124-127, 135-138
Question 47
An enterprise with global sites processes and exchanges highly sensitive information that is protected under several countries’ arms trafficking laws. There is new information that malicious nation-state-sponsored activities are targeting the use of encryption between the geographically
disparate sites. The organization currently employs ECDSA and ECDH with P-384, SHA-384, and AES- 256-GCM on VPNs between sites. Which of the following techniques would MOST likely improve the resilience of the enterprise to attack on cryptographic implementation?
Correct Answer:C
Question 48
Executive management is asking for a new manufacturing control and workflow automation solution. This application will facilitate management of proprietary information and closely guarded corporate trade secrets.
The information security team has been a part of the department meetings and come away with the following notes:
Human resources would like complete access to employee data stored in the application. They would like automated data interchange with the employee management application, a cloud-based SaaS application.
Sales is asking for easy order tracking to facilitate feedback to customers.
Legal is asking for adequate safeguards to protect trade secrets. They are also concerned with data ownership questions and legal jurisdiction.
Manufacturing is asking for ease of use. Employees working the assembly line cannot be bothered with additional steps or overhead. System interaction needs to be quick and easy.
Quality assurance is concerned about managing the end product and tracking overall performance of the product being produced. They would like read-only access to the entire workflow process for monitoring and baselining.
The favored solution is a user friendly software application that would be hosted onsite. It has extensive ACL functionality, but also has readily available APIs for extensibility. It supports read-only access, kiosk automation, custom fields, and data encryption.
Which of the following departments’ request is in contrast to the favored solution?
Correct Answer:E
The human resources department wanted complete access to employee data stored in the application, and an automated data interchange with their cloud-based SaaS employee management application. However, the favored solution provides read-only access and is hosted onsite. Incorrect Answers:
A: The manufacturing department wanted a quick and easy user friendly system. The favored solution is a user friendly software application that would meet the manufacturing department’s requests.
B: The legal department wanted a system that provides adequate safeguards to protect trade secrets and was concerned with data ownership and legal jurisdiction. The favored solution is a user friendly software application that would be hosted onsite. This would address the legal department’s concerns with data ownership and legal jurisdiction. The application also provides data encryption, which would protect trade secrets.
C: The sales department wanted an easy order tracking to facilitate feedback to customers. The favored solution is a user friendly software application that supports custom fields, which could be used for order tracking.
D: The quality assurance department was concerned about managing the end product and tracking overall performance. They also wanted read-only access to the entire workflow process for monitoring and baselining. These are met by the favored solution.