Online CAS-003 Practice TestMore CompTIA Products >
Free CompTIA CAS-003 Exam Dumps Questions
CompTIA CAS-003: CompTIA Advanced Security Practitioner (CASP)
- Get instant access to CAS-003 practice exam questions
- Get ready to pass the CompTIA Advanced Security Practitioner (CASP) exam right now using our CompTIA CAS-003 exam package, which includes CompTIA CAS-003 practice test plus an CompTIA CAS-003 Exam Simulator.
- The best online CAS-003 exam study material and preparation tool is here.
Question 1
During a recent audit of servers, a company discovered that a network administrator, who required
remote access, had deployed an unauthorized remote access application that communicated over common ports already allowed through the firewall. A network scan showed that this remote access application had already been installed on one third of the servers in the company. Which of the following is the MOST appropriate action that the company should take to provide a more appropriate solution?
Correct Answer:C
A Secure Sockets Layer (SSL) virtual private network (VPN) would provide the network administrator who requires remote access a secure and reliable method of accessing the system over the Internet. Security Assertion Markup Language (SAML) standards for federation will provide cross-web service authentication and authorization.
Incorrect Answers:
A: Blocking the application would prevent the network administrator who requires remote access from accessing the system. While this will address the presence of the unauthorized remote access application, it will not address the network administrator’s need for remote access.
B: Installing the unauthorized remote access application on the rest of the servers would not be an “appropriate” solution. An appropriate solution would provide a secure form of remote access to the network administrator who requires remote access.
D: An access control list (ACL) is used for packer filtering and for selecting types of traffic to be analyzed, forwarded, or blocked by the firewall or device. The ACL may block traffic based on source and destination address, interface, port, protocol, thresholds and various other criteri
A. However,
network address translation (NAT) is not used for remote access. It is used to map private IPv4 addresses to a single public IPv4 address, allowing multiple internal hosts with private IPv4 addresses to access the internet via the public IPv4 address.
References:
BOOK pp. 28, 40-41, 110-112, 138. 335-336 htHYPERLINK
"https://en.wikipedia.org/wiki/Network_address_translation"tps://en.wikipedia.org/wiki/Network_ address_translation
Question 2
An internal staff member logs into an ERP platform and clicks on a record. The browser URL changes to:
URL: http://192.168.0.100/ERP/accountId=5&action=SELECT
Which of the following is the MOST likely vulnerability in this ERP platform?
Correct Answer:C
Question 3
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
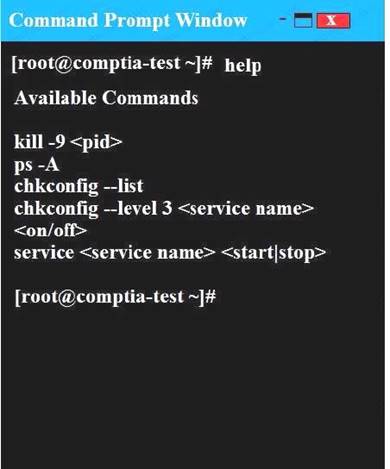
You may query help for a list of commands. Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Correct Answer:A
Question 4
A Chief Information Security Officer (CISO) has requested that a SIEM solution be implemented. The CISO wants to know upfront what the projected TCO would be before looking further into this concern. Two vendor proposals have been received:
Vendor A: product-based solution which can be purchased by the pharmaceutical company.
Capital expenses to cover central log collectors, correlators, storage and management consoles expected to be $150,000. Operational expenses are expected to be a 0.5 full time employee (FTE) to manage the solution, and 1 full time employee to respond to incidents per year.
Vendor B: managed service-based solution which can be the outsourcer for the pharmaceutical company’s needs.
Bundled offering expected to be $100,000 per year.
Operational expenses for the pharmaceutical company to partner with the vendor are expected to be a 0.5 FTE per year.
Internal employee costs are averaged to be $80,000 per year per FTE. Based on calculating TCO of the two vendor proposals over a 5 year period, which of the following options is MOST accurate?
Correct Answer:A
The costs of making use of an outsources solution will actually be a savings for the company thus the outsourced solution is a cheaper option over a 5 year period because it amounts to 0,5 FTE per year for the company and at present the company expense if $80,000 per year per FTE.
For the company to go alone it will cost $80,000 per annum per FTE = $400,000 over 5 years. With Vendor a $150,000 + $200,000 (½ FTE) = $350,000
With Vendor B = $100,000 it will be more expensive. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 130
Question 5
A software development manager is running a project using agile development methods. The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project.
Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?
Correct Answer:D
Question 6
A new cluster of virtual servers has been set up in a lab environment and must be audited before being allowed on the production network. The security manager needs to ensure unnecessary services are disabled and all system accounts are using strong credentials. Which of the following tools should be used? (Choose two.)
Correct Answer:BF