Question 19
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
Correct Answer:C
Question 20
What does ICMP Type 3/Code 13 mean?
Correct Answer:D
Question 21
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
Correct Answer:B
Question 22
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
Correct Answer:D
Question 23
War Driving is the act of moving around a specific area, mapping the population of wireless access points for statistical purposes. These statistics are then used to raise awareness of the security problems associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector) problem
documented with static WEP?
Correct Answer:A
Question 24
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.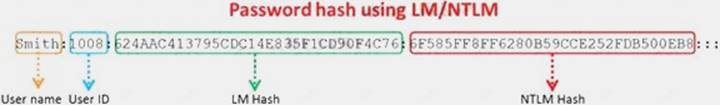
The SAM file in Windows Server 2008 is located in which of the following locations?
Correct Answer:D