Question 7
What operating system would respond to the following command?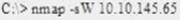
Correct Answer:D
Question 8
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers.
Which one of the following cannot handle routing protocols properly?
Correct Answer:B
Question 9
Which one of the following acts makes reputational risk of poor security a reality because it requires public disclosure of any security breach that involves personal information if it is unencrypted or if it is reasonably believed that the information has been acquired by an unauthorized person?
Correct Answer:A
Question 10
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive.org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code.
While searching through the code, you come across something abnormal:>><>
Correct Answer:C
Question 11
As a security analyst you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
Correct Answer:C
Question 12
Which one of the following 802.11 types has WLAN as a network support?
Correct Answer:C