Question 7
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
Correct Answer:D
Question 8
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
Correct Answer:C
Question 9
Refer to the exhibit.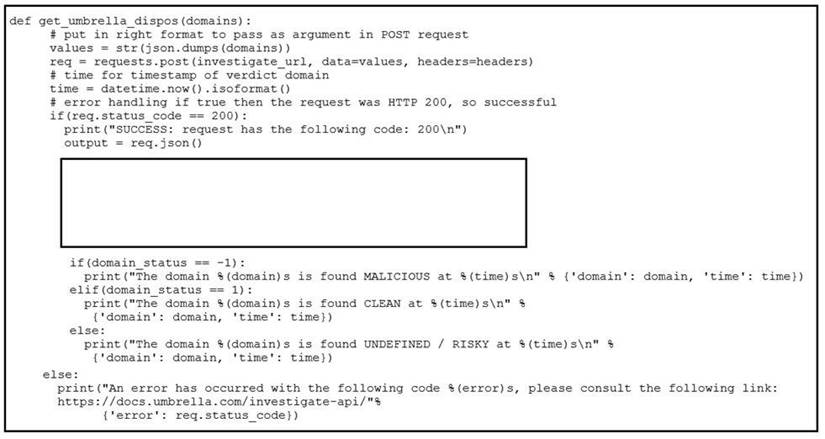
Which code snippet will parse the response to identify the status of the domain as malicious, clean or undefined?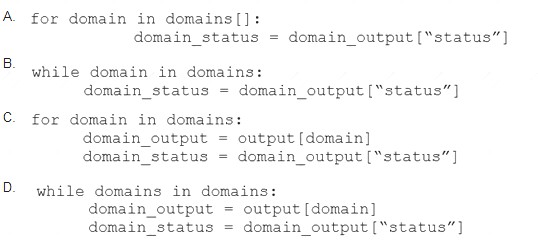
Correct Answer:C
Question 10
A SOC analyst is notified by the network monitoring tool that there are unusual types of internal traffic on IP subnet 103.861.2117.0/24. The analyst discovers unexplained encrypted data files on a computer system that belongs on that specific subnet. What is the cause of the issue?
Correct Answer:D
Question 11
Refer to the exhibit.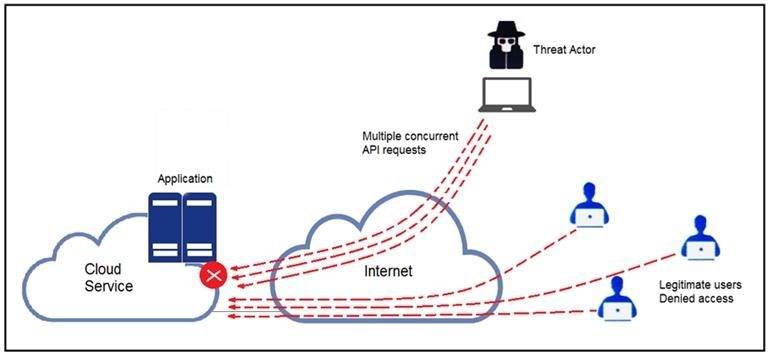
A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?
Correct Answer:A
Question 12
The incident response team receives information about the abnormal behavior of a host. A malicious file is found being executed from an external USB flash drive. The team collects and documents all the necessary evidence from the computing resource. What is the next step?
Correct Answer:B