Online 350-201 Practice TestMore Cisco Products >
Free Cisco 350-201 Exam Dumps Questions
Cisco 350-201: Performing CyberOps Using Core Security Technologies (CBRCOR)
- Get instant access to 350-201 practice exam questions
- Get ready to pass the Performing CyberOps Using Core Security Technologies (CBRCOR) exam right now using our Cisco 350-201 exam package, which includes Cisco 350-201 practice test plus an Cisco 350-201 Exam Simulator.
- The best online 350-201 exam study material and preparation tool is here.
Question 1
How is a SIEM tool used?
Correct Answer:D
Question 2
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
Correct Answer:D
Question 3
An organization lost connectivity to critical servers, and users cannot access business applications and internal websites. An engineer checks the network devices to investigate the outage and determines that all devices are functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not all options are used.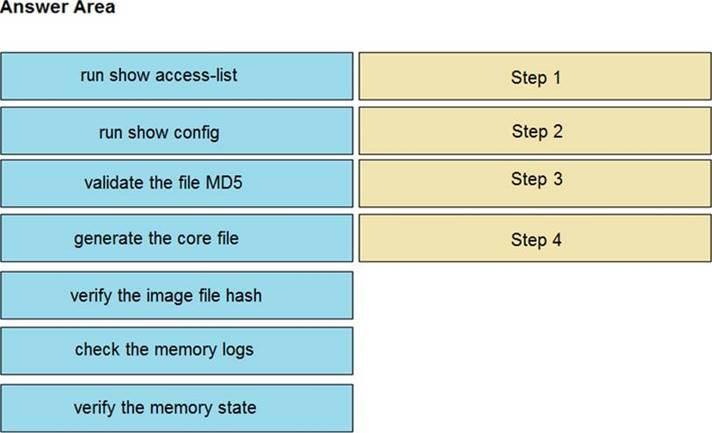
Solution: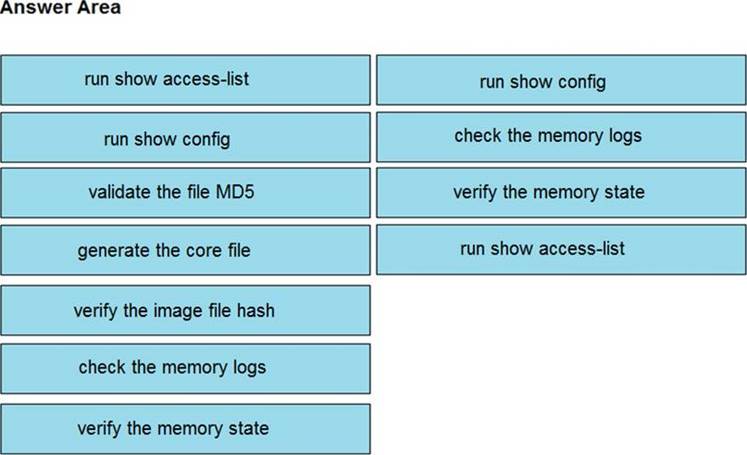
Does this meet the goal?
Correct Answer:A
Question 4
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company’s infrastructure. Which steps should an engineer take at the recovery stage?
Correct Answer:B
Question 5
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
Correct Answer:B
Question 6
Refer to the exhibit.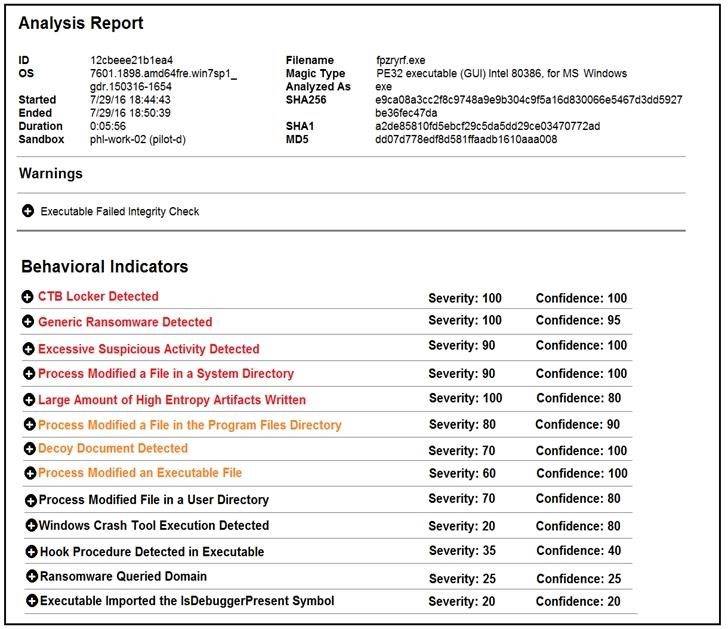
Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?
Correct Answer:C