Question 49
Which of the following is a component of a risk assessment?
Correct Answer:A
Question 50
Which system consists of a publicly available set of databases that contain domain name registration contact information?
Correct Answer:A
Question 51
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.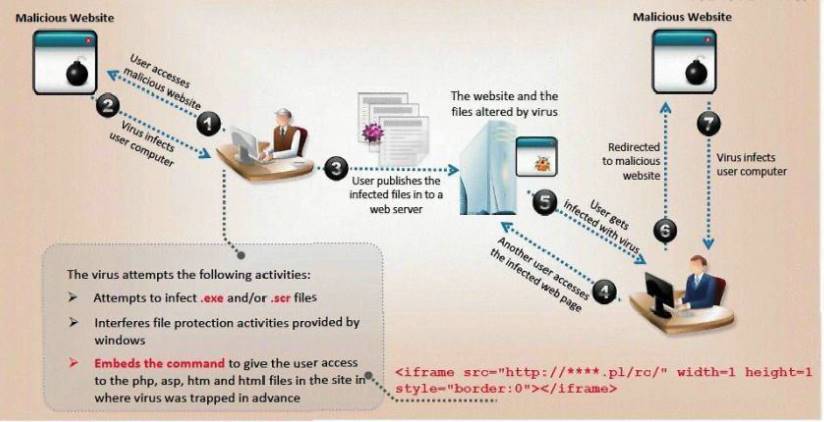
Here is a section of the Virus code: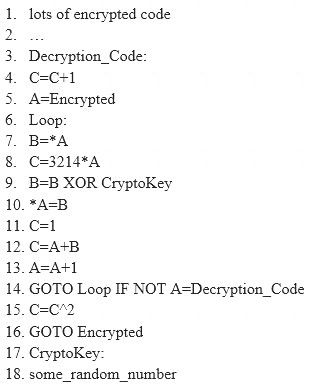
What is this technique called?
Correct Answer:A
Question 52
What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS?
Correct Answer:A
Question 53
What is the BEST alternative if you discover that a rootkit has been installed on one of your computers?
Correct Answer:E
Question 54
Tess King is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc) for a Domain.
What do you think Tess King is trying to accomplish? Select the best answer.
Correct Answer:B