Question 49
- (Topic 5)
An attacker runs netcat tool to transfer a secret file between two hosts.
Machine A: netcat -l -p 1234 < secretfile> 1234
He is worried about information being sniffed on the network. How would the attacker use netcat to encrypt the information before transmitting onto the wire?
Correct Answer:D
Netcat cannot encrypt the file transfer itself but would need to use a third
party application to encrypt/decrypt like openssl. Cryptcat is the standard netcat enhanced with twofish encryption.
Question 50
- (Topic 15)
On wireless networks, SSID is used to identify the network. Why are SSID not
considered to be a good security mechanism to protect a wireless networks?
Correct Answer:B
The SSID IS constructed to identify a network, it IS NOT the same as the MAC address and SSID’s consists of a maximum of 32 alphanumeric characters.
Question 51
- (Topic 5)
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
Correct Answer:C
All are DDOS tools.
Question 52
- (Topic 19)
Exhibit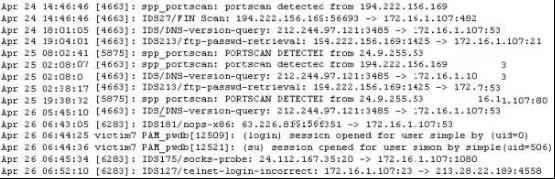
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
Correct Answer:C
According to the exhibit, the question is regarding the DNS Zone Transfer. Since Zone Transfers are done with TCP port 53, you should not allow this connect external to you organization.
Question 53
- (Topic 23)
Peter extracts the SID list from Windows 2008 Server machine using the hacking tool "SIDExtracter". Here is the output of the SIDs: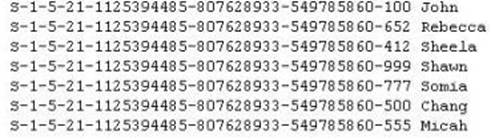
From the above list identify the user account with System Administrator privileges?
Correct Answer:F
Question 54
- (Topic 5)
A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems. However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
Correct Answer:B
In a Windows 2000 network using Kerberos you normally use pre- authentication and the user password never leaves the local machine so it is never exposed to the network so it should not be able to be sniffed.