Question 43
- (Topic 18)
You have just installed a new Linux file server at your office. This server is going to be used by several individuals in the organization, and unauthorized personnel must not be able to modify any data.
What kind of program can you use to track changes to files on the server?
Correct Answer:C
System Integrity Verifiers like Tripwire aids system administrators and users
in monitoring a designated set of files for any changes. Used with system files on a regular (e.g., daily) basis, Tripwire can notify system administrators of corrupted or tampered files, so damage control measures can be taken in a timely manner.
Question 44
- (Topic 9)
Within the context of Computer Security, which of the following statements best
describe Social Engineering?
Correct Answer:B
Social engineering is a collection of techniques used to manipulate people into performing actions or divulging confidential information.
Question 45
- (Topic 3)
Name two software tools used for OS guessing.(Choose two.
Correct Answer:AC
Nmap and Queso are the two best-known OS guessing programs. OS guessing software has the ability to look at peculiarities in the way that each vendor implements the RFC's. These differences are compared with its database of known OS fingerprints. Then a best guess of the OS is provided to the user.
Question 46
- (Topic 3)
While reviewing the result of scanning run against a target network you come across the following: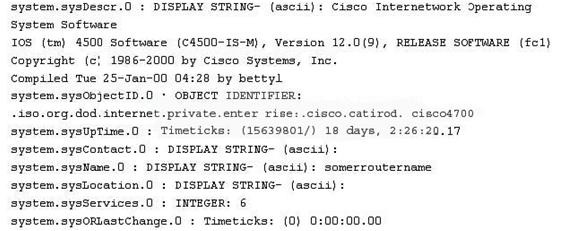
Which among the following can be used to get this output?
Correct Answer:D
SNMP lets you "read" information from a device. You make a query of the server (generally known as the "agent"). The agent gathers the information from the host system and returns the answer to your SNMP client. It's like having a single interface for all
your informative Unix commands. Output like system.sysContact.0 is called a MIB.
Question 47
- (Topic 9)
Sabotage, Advertising and Covering are the three stages of
Correct Answer:B
Typical social interaction dictates that if someone gives us something then it is only right for us to return the favour. This is known as reverse social engineering, when an attacker sets up a situation where the victim encounters a problem, they ask the attacker for help and once the problem is solved the victim then feels obliged to give the information requested by the attacker.
Question 48
- (Topic 23)
TCP/IP Session Hijacking is carried out in which OSI layer?
Correct Answer:A