Question 37
- (Topic 1)
What does the term “Ethical Hacking” mean?
Correct Answer:C
Ethical hacking is only about defending your self or your employer against malicious persons by using the same techniques and skills.
Question 38
- (Topic 23)
Which port, when configured on a switch receives a copy of every packet that passes through it?
Correct Answer:C
Question 39
- (Topic 20)
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect’s workstation. He comes across a file that is called ‘file.txt’ but when he opens it, he find the following: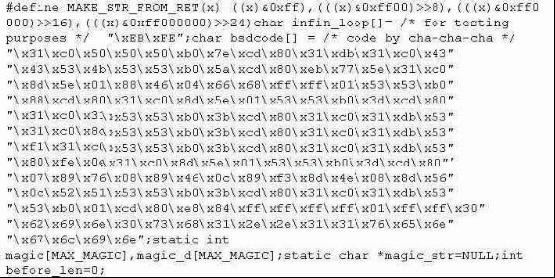
What does this file contain?
Correct Answer:D
This is a buffer overflow exploit with its “payload” in hexadecimal format.
Question 40
- (Topic 23)
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
Correct Answer:D
Question 41
- (Topic 23)
What is the correct order of steps in CEH System Hacking Cycle?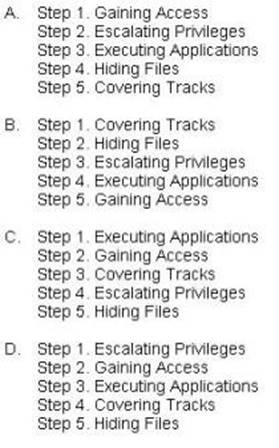
Correct Answer:A
Question 42
- (Topic 22)
A client has approached you with a penetration test requirements. They are concerned with the possibility of external threat, and have invested considerable resources in protecting their Internet exposure. However, their main concern is the possibility of an employee elevating his/her privileges and gaining access to information outside of their respective department.
What kind of penetration test would you recommend that would best address the client’s concern?
Correct Answer:C