Question 31
- (Topic 23)
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be the first step the attacker would perform?
Correct Answer:C
Question 32
- (Topic 15)
Why do you need to capture five to ten million packets in order to crack WEP with AirSnort?
Correct Answer:C
Since the summer of 2001, WEP cracking has been a trivial but time consuming process. A few tools, AirSnort perhaps the most famous, that implement the Fluhrer-Mantin-Shamir (FMS) attack were released to the security community -- who until then were aware of the problems with WEP but did not have practical penetration testing
tools. Although simple to use, these tools require a very large number of packets to be gathered before being able to crack a WEP key. The AirSnort web site estimates the total number of packets at five to ten million, but the number actually required may be higher than you think.
Question 33
- (Topic 8)
SYN Flood is a DOS attack in which an attacker deliberately violates the three-way handshake and opens a large number of half-open TCP connections.
The signature for SYN Flood attack is:
Correct Answer:C
A SYN attack occurs when an attacker exploits the use of the buffer space during a Transmission Control Protocol (TCP) session initialization handshake. The attacker floods the target system's small "in-process" queue with connection requests, but it does not respond when a target system replies to those requests. This causes the target system to time out while waiting for the proper response, which makes the system crash or become unusable.
Question 34
- (Topic 23)
Giles is the network administrator for his company, a graphics design company based in Dallas. Most of the network is comprised of Windows servers and workstations, except for some designers that prefer to use MACs. These MAC users are running on the MAC OS X operating system. These MAC users also utilize iChat to talk between each other. Tommy, one of these MAC users, calls Giles and says that his computer is running very slow. Giles then gets more calls from the other MAC users saying they are receiving instant messages from Tommy even when he says he is not on his computer. Giles immediately unplugs Tommy's computer from the network to take a closer look. He opens iChat on Tommy's computer and it says that it sent a file called latestpics.tgz to all the other MAC users. Tommy says he never sent those files. Giles also sees that many of the computer's applications appear to be altered. The path where the files should be has an altered file and the original application is stored in the file's resource fork.
What has Giles discovered on Tommy's computer?
Correct Answer:B
OSX.Leap.A is a worm that targets installs of Macintosh OS X and spreads via iChat Instant Messenger program. http://www.symantec.com/security_response/writeup.jsp?docid=2006-021614-4006-99
Question 35
- (Topic 3)
Exhibit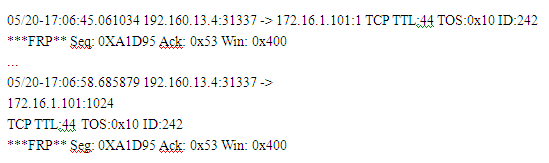
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
Correct Answer:B
Port 31337 is normally used by Back Orifice. Note that 31337 is hackers spelling of ‘elite’, meaning ‘elite hackers’.
Question 36
- (Topic 8)
If you send a SYN to an open port, what is the correct response?(Choose all correct answers.
Correct Answer:AB
The proper response is a SYN / ACK. This technique is also known as half- open scanning.