Question 145
- (Topic 15)
Bob reads an article about how insecure wireless networks can be. He gets approval from his management to implement a policy of not allowing any wireless devices on the network. What other steps does Bob have to take in order to successfully implement this? (Select 2 answer.)
Correct Answer:AD
If someone installs a access point and connect it to the network there is no way to find it unless you are constantly surveying the area for wireless devices. SNMP and firewalls can not prevent the installation of wireless devices on the corporate network.
Question 146
- (Topic 23)
Jason is the network administrator of Spears Technology. He has enabled SNORT IDS to detect attacks going through his network. He receives Snort SMS alerts on his iPhone whenever there is an attempted intrusion to his network.
He receives the following SMS message during the weekend.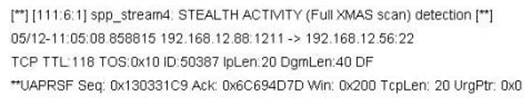
An attacker Chew Siew sitting in Beijing, China had just launched a remote scan on Jason's network with the hping command.
Which of the following hping2 command is responsible for the above snort alert?
Correct Answer:A
Question 147
- (Topic 3)
Which of the following Nmap commands would be used to perform a UDP scan of the lower 1024 ports?
Correct Answer:C
Nmap -sU -p 1-1024 <hosts.> is the proper syntax. Learning Nmap and its switches are critical for successful completion of the CEH exam.
Question 148
- (Topic 18)
You are trying to compromise a Linux Machine and steal the password hashes for cracking with password brute forcing program. Where is the password file kept is Linux?
Correct Answer:A
/etc/shadow file stores actual password in encrypted format for user’s account with additional properties related to user password i.e. it stores secure user account information. All fields are separated by a colon (:) symbol. It contains one entry per line for each user listed in /etc/passwd file.
Question 149
- (Topic 23)
In which part of OSI layer, ARP Poisoning occurs?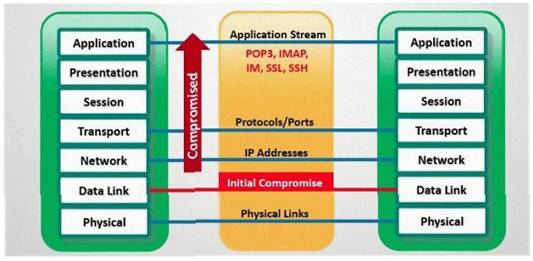
Correct Answer:B
Question 150
- (Topic 23)
Perimeter testing means determining exactly what your firewall blocks and what it allows. To conduct a good test, you can spoof source IP addresses and source ports. Which of the following command results in packets that will appear to originate from the system at 10.8.8.8? Such a packet is useful for determining whether the firewall is allowing random packets in or out of your network.
Correct Answer:D