Question 121
- (Topic 15)
Jackson discovers that the wireless AP transmits 128 bytes of plaintext, and the station responds by encrypting the plaintext. It then transmits the resulting ciphertext using the same key and cipher that are used by WEP to encrypt subsequent network traffic. What authentication mechanism is being followed here?
Correct Answer:C
The following picture shows how the WEP authentication procedure: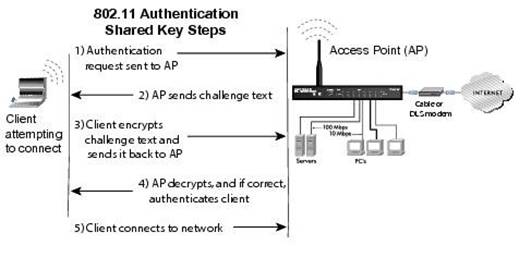
Question 122
- (Topic 3)
What is the proper response for a X-MAS scan if the port is open?
Correct Answer:F
Closed ports respond to a X-MAS scan by ignoring the packet.
Question 123
- (Topic 23)
The GET method should never be used when sensitive data such as credit card is being sent to a CGI program. This is because any GET command will appear in the URL, and will be logged by any servers. For example, let's say that you've entered your credit card information into a form that uses the GET method. The URL may appear like this:
https://www.xsecurity-bank.com/creditcard.asp?cardnumber=453453433532234
The GET method appends the credit card number to the URL. This means that anyone with access to a server log will be able to obtain this information. How would you protect from this type of attack?
Correct Answer:C
Question 124
- (Topic 18)
John is the network administrator of XSECURITY systems. His network was recently compromised. He analyzes the logfiles to investigate the attack.
Take a look at the following Linux logfile snippet. The hacker compromised and "owned" a Linux machine. What is the hacker trying to accomplish here?
[root@apollo /]# rm rootkit.c
[root@apollo /]# [root@apollo /]# ps -aux | grep inetd ; ps -aux | grep portmap ;
rm /sbin/portmap ; rm /tmp/h ; rm /usr/sbin/rpc.portmap ; rm -rf .bash* ; rm -
rf /root/.bash_history ; rm - rf /usr/sbin/namedps -aux | grep inetd ; ps -aux | grep portmap ; rm /sbin/por359 ? 00:00:00 inetd 359 ? 00:00:00 inetd
rm: cannot remove `/tmp/h': No such file or directory
rm: cannot remove `/usr/sbin/rpc.portmap': No such file or directory [root@apollo /]# ps -aux | grep portmap
[root@apollo /]# [root@apollo /]# ps -aux | grep inetd ; ps -aux | grep portmap ; rm
/sbin/portmap ;
rm /tmp/h ; rm /usr/sbin/rpc.portmap ; rm -rf .bash* ; rm -rf /root/.bash_history ; rm - rf /usr/sbin/namedps -aux | grep inetd ; ps -aux | grep portmap ; rm /sbin/por359 ? 00:00:00 inetd
rm: cannot remove `/sbin/portmap': No such file or directory rm: cannot remove `/tmp/h': No such file or directory
>rm: cannot remove `/usr/sbin/rpc.portmap': No such file or directory [root@apollo /]# rm: cannot remove `/sbin/portmap': No such file or directory
Correct Answer:B
By deleting temporary directories and emptying like bash_history that contains the last commands used with the bash shell he is trying to cover his tracks.
Question 125
- (Topic 14)
Your boss is attempting to modify the parameters of a Web-based application in order to alter the SQL statements that are parsed to retrieve data from the database. What would you call such an attack?
Correct Answer:D
This technique is known as SQL injection attack
Question 126
- (Topic 4)
SNMP is a connectionless protocol that uses UDP instead of TCP packets? (True or False)
Correct Answer:A
TCP and UDP provide transport services. But UDP was preferred. This is due to TCP characteristics, it is a complicate protocol and it consume to many memory and CPU resources. Where as UDP is easy to build and run. Into devices (repeaters and modems) vendors have built simple version of IP and UDP.