Question 103
- (Topic 19)
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot?
Select the best answers.
Correct Answer:ACDE
A low interaction honeypot would have emulators of vulnerable programs, not the real programs.
A high interaction honeypot is more likely to be penetrated as it is running the real program and is more vulnerable than an emulator.
Low interaction honeypots are easier to deploy and maintain. Usually you would just use a program that is already available for download and install it. Hackers don't usually crash or destroy these types of programs and it would require little maintenance.
A low interaction honeypot tends to be used for production.
Low interaction honeypots are more detectable because you are using emulators of the real programs. Many hackers will see this and realize that they are in a honeypot.
A low interaction honeypot tends to be used for production. A high interaction honeypot tends to be used for research.
Question 104
- (Topic 2)
Which of the following tools are used for footprinting?(Choose four.
Correct Answer:ABCD
All of the tools listed are used for footprinting except Cheops.
Question 105
- (Topic 2)
Your company trainee Sandra asks you which are the four existing Regional Internet Registry (RIR's)?
Correct Answer:B
All other answers include non existing organizations (PICNIC, NANIC, LATNIC). See http://www.arin.net/library/internet_info/ripe.html
Question 106
- (Topic 11)
Bart is looking for a Windows NT/2000/XP command-line tool that can be used to assign, display, or modify ACL’s (access control lists) to files or folders and also one that can be used within batch files.
Which of the following tools can be used for that purpose? (Choose the best answer)
Correct Answer:B
Cacls.exe is a Windows NT/2000/XP command-line tool you can use to assign, display, or modify ACLs (access control lists) to files or folders. Cacls is an interactive tool, and since it's a command-line utility, you can also use it in batch files.
Question 107
- (Topic 23)
A Trojan horse is a destructive program that masquerades as a benign application. The software initially appears to perform a desirable function for the user prior to installation and/or execution, but in addition to the expected function steals information or harms the system.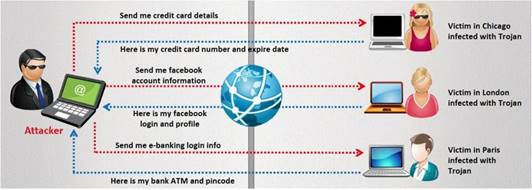
The challenge for an attacker is to send a convincing file attachment to the victim, which gets easily executed on the victim machine without raising any suspicion. Today's end
users are quite knowledgeable about malwares and viruses. Instead of sending games and fun executables, Hackers today are quite successful in spreading the Trojans using Rogue security software.
What is Rogue security software?
Correct Answer:BCD
Question 108
- (Topic 3)
John has performed a scan of the web server with NMAP but did not gather enough information to accurately identify which operating system is running on the remote host. How could you use a web server to help in identifying the OS that is being used?
Correct Answer:A
Most Web servers politely identify themselves and the OS to anyone who asks.