Question 97
- (Topic 19)
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application.
Which of the following strategies can be used to defeat detection by a network- based IDS application? (Choose the best answer)
Correct Answer:A
Certain types of encryption presents challenges to network-based intrusion detection and may leave the IDS blind to certain attacks, where a host-based IDS analyzes the data after it has been decrypted.
Question 98
- (Topic 3)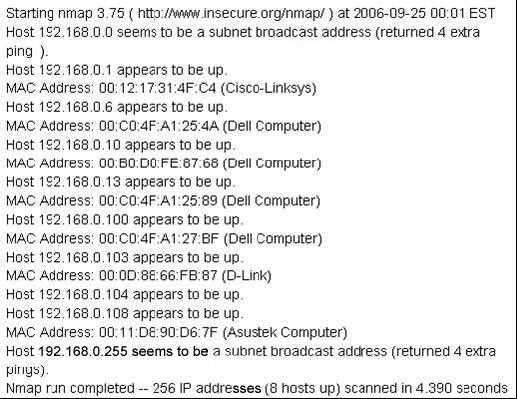
Which of the following nmap command in Linux procedures the above output?
Correct Answer:A
This is an output from a ping scan. The option –sP will give you a ping scan of the 192.168.0.1/24 network.
Question 99
- (Topic 23)
You want to perform advanced SQL Injection attack against a vulnerable website. You are unable to perform command shell hacks on this server. What must be enabled in SQL Server to launch these attacks?
Correct Answer:C
Question 100
- (Topic 23)
Your computer is infected by E-mail tracking and spying Trojan. This Trojan infects the computer with a single file - emos.sys
Which step would you perform to detect this type of Trojan?
Correct Answer:C
Question 101
- (Topic 7)
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
Correct Answer:C
Tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis or debugging. A program like 'tcpdump' shows a summary of packets seen on the wire, but usually doesn't store the data that's actually being transmitted. In contrast, tcpflow reconstructs the actual data streams and stores each flow in a separate file for later analysis.
Question 102
- (Topic 23)
Keystroke logging is the action of tracking (or logging) the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored.
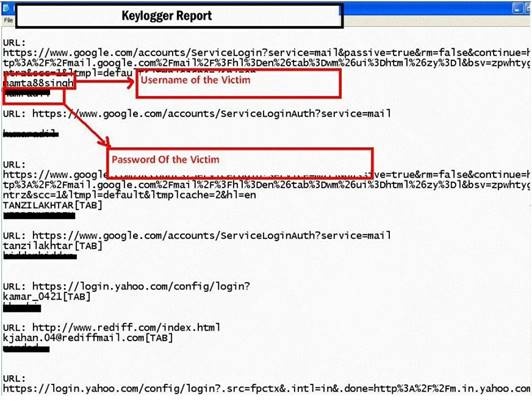
How will you defend against hardware keyloggers when using public computers and Internet Kiosks? (Select 4 answers)
Correct Answer:ACDE