Question 85
- (Topic 23)
In Trojan terminology, what is a covert channel?
Correct Answer:A
Question 86
- (Topic 20)
When writing shellcodes, you must avoid because these will end the string.
Correct Answer:A
The null character (also null terminator) is a character with the value zero, present in the ASCII and Unicode character sets, and available in nearly all mainstream programming languages. The original meaning of this character was like NOP — when sent to a printer or a terminal, it does nothing (some terminals, however, incorrectly display it as space). Strings ending in a null character are said to be null-terminated.
Question 87
- (Topic 11)
Which of the following buffer overflow exploits are related to Microsoft IIS web server? (Choose three)
Correct Answer:ABC
Both the buffer overflow in the Internet Printing Protocol and the ISAPI extension buffer overflow is explained in Microsoft Security Bulletin MS01-023. The Code Red worm was a computer worm released on the Internet on July 13, 2001. It attacked computers running Microsoft's IIS web server.
Question 88
- (Topic 9)
Usernames, passwords, e-mail addresses, and the location of CGI scripts may be obtained from which of the following information sources?
Correct Answer:A
Whois query would not enable us to find the CGI scripts whereas in the actual website, some of them will have scripts written to make the website more user friendly. The EDGAR database would in fact give us a lot of the information requested but not the location of CGI scripts, as would a simple search engine on the Internet if you have the time needed.
Question 89
- (Topic 4)
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
Correct Answer:D
NULL sessions take advantage of “features” in the SMB (Server Message Block) protocol that exist primarily for trust relationships. You can establish a NULL session with a Windows host by logging on with a NULL user name and password. Primarily the following ports are vulnerable if they are accessible:
139
TCP
NETBIOS Session Service 139
UDP
NETBIOS Session Service
445
TCP SMB/CIFS
Question 90
- (Topic 14)
Exhibit: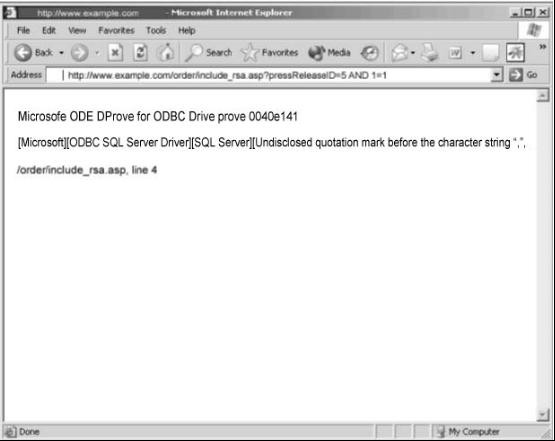
You are conducting pen-test against a company’s website using SQL Injection techniques. You enter “anuthing or 1=1-“ in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
Correct Answer:A