Question 79
- (Topic 12)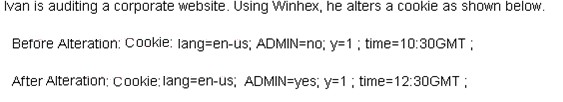
What attack is being depicted here?
Correct Answer:D
Manipulating the data sent between the browser and the web application to an attacker's advantage has long been a simple but effective way to make applications do things in a way the user often shouldn't be able to. In a badly designed and developed web application, malicious users can modify things like prices in web carts, session tokens or values stored in cookies and even HTTP headers. In this case the user has elevated his rights.
Question 80
- (Topic 23)
Marshall is the information security manager for his company. Marshall was just hired on two months ago after the last information security manager retired. Since the last manager did not implement or even write IT policies, Marshall has begun writing IT security policies to cover every conceivable aspect. Marshall's supervisor has informed him that while most employees will be under one set of policies, ten other employees will be under another since they work on computers in publicly-accessible areas. Per his supervisor, Marshall has written two sets of policies. For the users working on publicly-accessible computers, their policies state that everything is forbidden. They are not allowed to browse the Internet or even use email. The only thing they can use is their work related applications like Word and Excel.
What types of policies has Marshall written for the users working on computers in the publicly-accessible areas?
Correct Answer:C
It says that everything is forbidden, this means that there is a Paranoid Policy implemented
Question 81
- (Topic 22)
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
Correct Answer:D
Sending a bogus email is one way to find out more about internal servers. Also, to gather additional IP addresses and learn how they treat mail.
Question 82
- (Topic 18)
Windump is the windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform you must install a packet capture library.
What is the name of this library?
Correct Answer:C
WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
Question 83
- (Topic 3)
Which of the following systems would not respond correctly to an nmap XMAS
scan?
Correct Answer:A
When running a XMAS Scan, if a RST packet is received, the port is considered closed, while no response means it is open|filtered. The big downside is that not all systems follow RFC 793 to the letter. A number of systems send RST responses to the probes regardless of whether the port is open or not. This causes all of the ports to be labeled closed. Major operating systems that do this are Microsoft Windows, many Cisco devices, BSDI, and IBM OS/400.
Question 84
- (Topic 4)
Jess the hacker runs L0phtCrack’s built-in sniffer utility which grabs SMB password hashes and stores them for offline cracking. Once cracked, these passwords can provide easy access to whatever network resources the user account has access to.
But Jess is not picking up hashed from the network. Why?
Correct Answer:A
To protect against SMB session hijacking, NT supports a cryptographic integrity mechanism, SMB Signing, to prevent active network taps from interjecting themselves into an already established session.