Question 55
- (Topic 19)
Which of the following is not an effective countermeasure against replay attacks?
Correct Answer:C
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. Effective countermeasures should be
anything that makes it hard to delay or replay the packet (time stamps and sequence numbers) or anything that prove the package is received as it was sent from the original sender (digital signature)
Question 56
- (Topic 23)
What type of port scan is represented here.
Correct Answer:A
Question 57
- (Topic 10)
John is using tokens for the purpose of strong authentication. He is not confident that his security is considerably strong.
In the context of Session hijacking why would you consider this as a false sense of security?
Correct Answer:B
A token will give you a more secure authentication, but the tokens will not help against attacks that are directed against you after you have been authenticated.
Question 58
- (Topic 7)
How would you describe a simple yet very effective mechanism for sending and receiving unauthorized information or data between machines without alerting any firewalls and IDS's on a network?
Correct Answer:A
A covert channel is described as: "any communication channel that can be exploited by a process to transfer information in a manner that violates the systems security policy." Essentially, it is a method of communication that is not part of an actual computer system design, but can be used to transfer information to users or system processes that normally would not be allowed access to the information.
Question 59
- (Topic 23)
You establish a new Web browser connection to Google. Since a 3-way handshake is required for any TCP connection, the following actions will take place.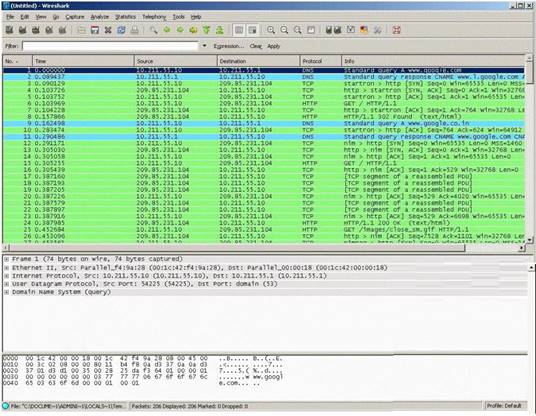
✑ DNS query is sent to the DNS server to resolve www.google.com
✑ DNS server replies with the IP address for Google?
✑ SYN packet is sent to Google.
✑ Google sends back a SYN/ACK packet
✑ Your computer completes the handshake by sending an ACK
✑ The connection is established and the transfer of data commences
Which of the following packets represent completion of the 3-way handshake?
Correct Answer:D
Question 60
- (Topic 3)
While doing fast scan using –F option, which file is used to list the range of ports to scan by nmap?
Correct Answer:B
Nmap uses the nmap-services file to provide additional port detail for almost every scanning method. Every time a port is referenced, it's compared to an available description in this support file. If the nmap-services file isn't available, nmap reverts to the /etc/services file applicable for the current operating system.