Online 312-50 Practice TestMore EC-Council Products >
Free EC-Council 312-50 Exam Dumps Questions
EC-Council 312-50: Ethical Hacking and Countermeasures (CEHv6)
- Get instant access to 312-50 practice exam questions
- Get ready to pass the Ethical Hacking and Countermeasures (CEHv6) exam right now using our EC-Council 312-50 exam package, which includes EC-Council 312-50 practice test plus an EC-Council 312-50 Exam Simulator.
- The best online 312-50 exam study material and preparation tool is here.
Question 1
- (Topic 5)
Which of the following is the primary objective of a rootkit?
Correct Answer:C
Actually the objective of the rootkit is more to hide the fact that a system has been compromised and the normal way to do this is by exchanging, for example, ls to a version that doesn’t show the files and process implanted by the attacker.
Question 2
- (Topic 19)
Angela is trying to access an education website that requires a username and password to login. When Angela clicks on the link to access the login page, she gets an error message stating that the page can’t be reached. She contacts the website’s support team and they report that no one else is having any issues with the site. After handing the issue over to her company’s IT department, it is found that the education website requires any computer accessing the site must be able to respond to a ping from the education’s server. Since Angela’s computer is behind a corporate firewall, her computer can’t ping the education website back.
What ca Angela’s IT department do to get access to the education website?
Correct Answer:A
Allowing traffic to and from port 80 will not help as this will be UDP or TCP traffic and ping uses ICMP. The browser used by the user will not make any difference. The only alternative here that would solve the problem is to move the computer to outside the firewall.
Question 3
- (Topic 19)
Basically, there are two approaches to network intrusion detection: signature detection, and anomaly detection. The signature detection approach utilizes well- known signatures for network traffic to identify potentially malicious traffic. The anomaly detection approach utilizes a previous history of network traffic to search for patterns that are abnormal, which would indicate an intrusion. How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of his attack going undetected by the IDS?
Correct Answer:D
ADMmutate is using a polymorphic technique designed to circumvent certain forms of signature based intrusion detection. All network based remote buffer overflow exploits have similarities in how they function. ADMmutate has the ability to emulate the protocol of the service the attacker is attempting to exploit. The data payload (sometimes referred to as an egg) contains the instructions the attacker wants to execute on the target machine. These eggs are generally interchangeable and can be utilized in many different buffer overflow exploits. ADMmutate uses several techniques to randomize the contents of the egg in any given buffer overflow exploit. This randomization effectively changes the content or 'signature' of the exploit without changing the functionality of the exploit.
Question 4
- (Topic 23)
What type of Virus is shown here?
Correct Answer:E
Question 5
- (Topic 8)
What do you call a system where users need to remember only one username and password, and be authenticated for multiple services?
Correct Answer:C
Single sign-on (SSO) is a specialized form of software authentication that enables a user to authenticate once and gain access to the resources of multiple software systems.
Question 6
- (Topic 23)
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.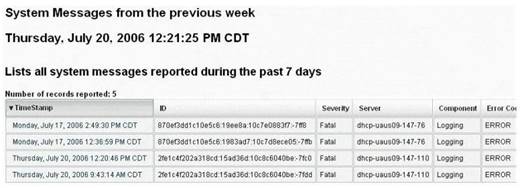
What default port Syslog daemon listens on?
Correct Answer:D