Question 103
- (Exam Topic 2)
When operating systems mark a cluster as used but not allocated, the cluster is considered as ________
Correct Answer:C
Question 104
- (Exam Topic 2)
While looking through the IIS log file of a web server, you find the following entries: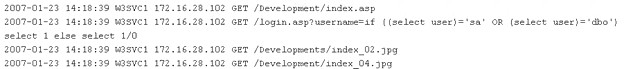
What is evident from this log file?
Correct Answer:D
Question 105
- (Exam Topic 1)
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, stateful firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet. Why is that?
Correct Answer:D
Question 106
- (Exam Topic 2)
Paraben Lockdown device uses which operating system to write hard drive data?
Correct Answer:D
Question 107
- (Exam Topic 2)
Which of the following tool can the investigator use to analyze the network to detect Trojan activities?
Correct Answer:D
Question 108
- (Exam Topic 3)
The MAC attributes are timestamps that refer to a time at which the file was last modified or last accessed or originally created. Which of the following file systems store MAC attributes in Coordinated Universal Time (UTC) format?
Correct Answer:B