Question 7
A software company wants to protect its source code, including new source code created between scheduled indexing runs. Which detection method should the company use to meet this requirement?
Correct Answer:D
Reference: https://help.symantec.com/cs/DLP15.0/DLP/v100774847_v120691346/Scheduling-remote-indexing?locale=EN_US
Question 8
What is required on the Enforce server to communicate with the Symantec DLP database?
Correct Answer:D
Reference: https://www.symantec.com/connect/articles/three-tier-installation-dlp-product
Question 9
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a “copy to USB device” operation?
Correct Answer:A
Question 10
Which channel does Endpoint Prevent protect using Device Control?
Correct Answer:B
Reference: https://support.symantec.com/en_US/article.HOWTO80865.html#v36651044
Question 11
Which server target uses the “Automated Incident Remediation Tracking” feature in Symantec DLP?
Correct Answer:B
Reference: https://help.symantec.com/cs/DLP15.0/DLP/v83981880_v120691346/Troubleshooting-automated-incident-remediation-tracking?locale=EN_US
Question 12
Refer to the exhibit.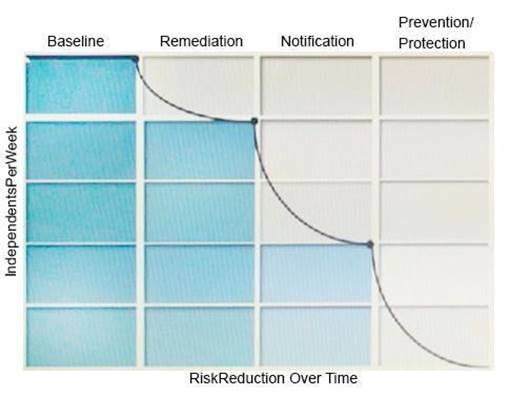
What activity should occur during the baseline phase, according to the risk reduction model?
Correct Answer:C