Question 19
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Correct Answer:D
Question 20
Which type of data collection requires the largest amount of storage space?
Correct Answer:D
Question 21
Which incidence response step includes identifying all hosts affected by an attack'?
Correct Answer:A
Question 22
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
Correct Answer:D
Question 23
Refer to the exhibit.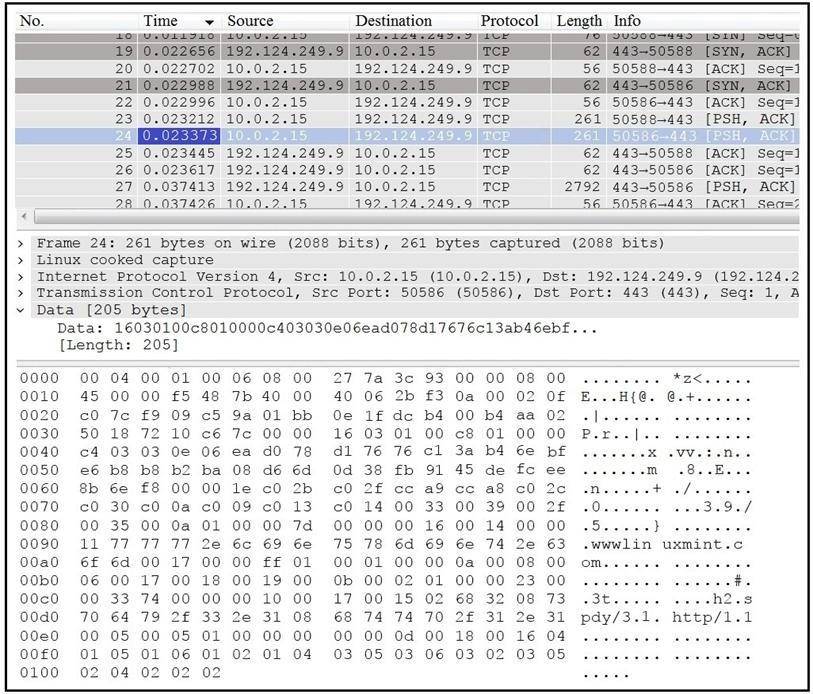
Which application protocol is in this PCAP file?
Correct Answer:B
Question 24
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
Correct Answer:D