Question 13
Drag and drop the security concept on the left onto the example of that concept on the right.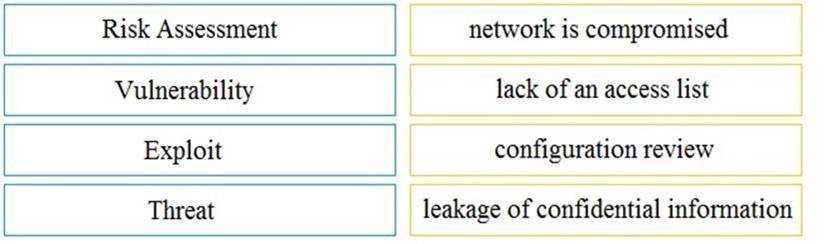
Solution:
Does this meet the goal?
Correct Answer:A
Question 14
How is attacking a vulnerability categorized?
Correct Answer:C
Question 15
Which artifact is used to uniquely identify a detected file?
Correct Answer:D
Question 16
Refer to the exhibit.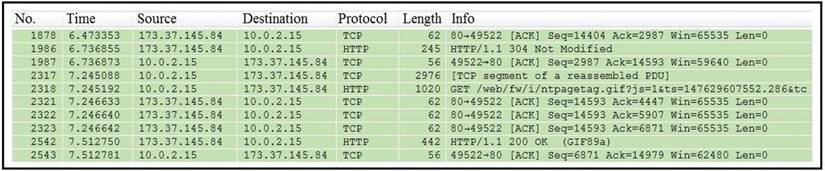
Which packet contains a file that is extractable within Wireshark?
Correct Answer:D
Question 17
Why is encryption challenging to security monitoring?
Correct Answer:B
Question 18
Drag and drop the access control models from the left onto the correct descriptions on the right.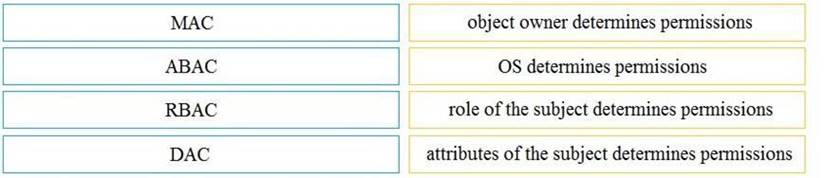
Solution: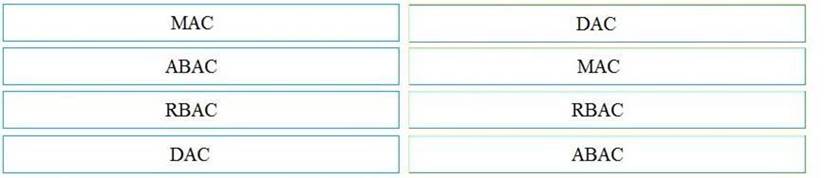
Does this meet the goal?
Correct Answer:A