Question 7
What does an attacker use to determine which network ports are listening on a potential target device?
Correct Answer:B
Question 8
What is a difference between SOAR and SIEM?
Correct Answer:A
Question 9
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
Correct Answer:A
Question 10
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
Correct Answer:C
Question 11
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.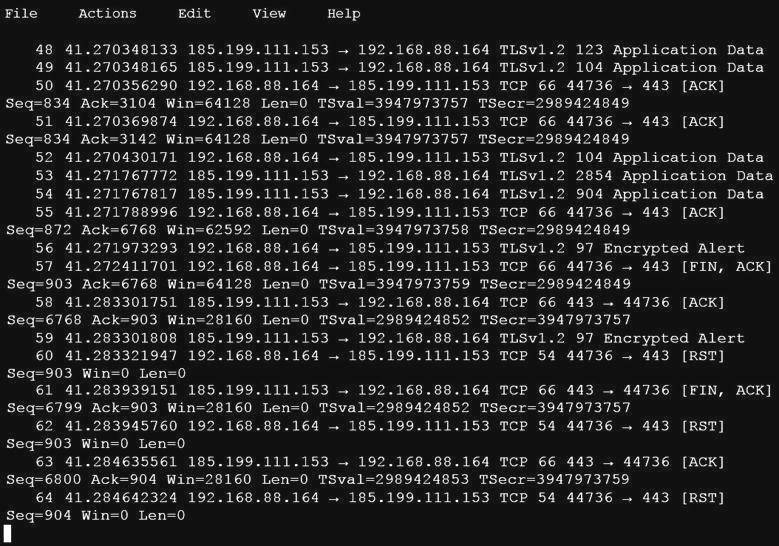
Which obfuscation technique is the attacker using?
Correct Answer:B
Question 12
Refer to the exhibit.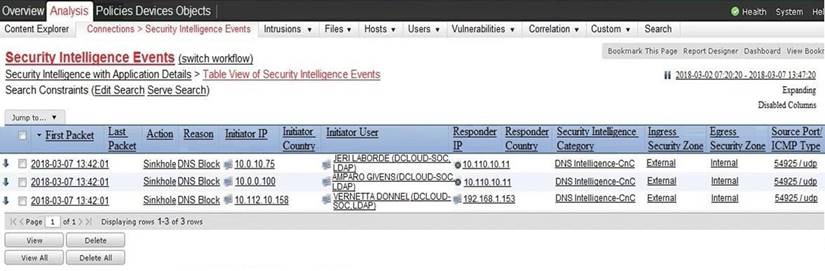
Which two elements in the table are parts of the 5-tuple? (Choose two.)
Correct Answer:DE