Question 13
- (Exam Topic 1)
On the following graphic, you will find layers of policies.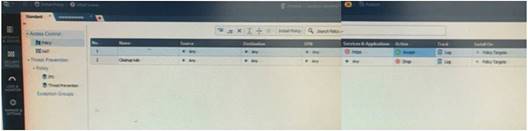
What is a precedence of traffic inspection for the defined polices?
Correct Answer:B
To simplify Policy management, R80 organizes the policy into Policy Layers. A layer is a set of rules, or a Rule Base.
For example, when you upgrade to R80 from earlier versions:
Gateways that have the Firewall and the Application Control Software Blades enabled will have their Access Control Policy split into two ordered layers: Network and Applications.
When the gateway matches a rule in a layer, it starts to evaluate the rules in the next layer.
Gateways that have the IPS and Threat Emulation Software Blades enabled will have their Threat Prevention policies split into two parallel layers: IPS and Threat Prevention.
All layers are evaluated in parallel
When the gateway matches a rule in a layer, it starts to evaluate the rules in the next layer.
All layers are evaluated in parallel
Question 14
- (Exam Topic 4)
In the Check Point Security Management Architecture, which component(s) can store logs?
Correct Answer:B
Question 15
- (Exam Topic 3)
Which of the following uses the same key to decrypt as it does to encrypt?
Correct Answer:D
Question 16
- (Exam Topic 2)
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ___ all traffic. However, in the Application Control policy layer, the default action is _____ all traffic.
Correct Answer:D
Question 17
- (Exam Topic 4)
Using R80 Smart Console, what does a “pencil icon” in a rule mean?
Correct Answer:A
Question 18
- (Exam Topic 1)
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
Correct Answer:A
Authentication Schemes :- Check Point Password
- Operating System Password
- RADIUS
- SecurID
- TACAS
- Undefined If a user with an undefined authentication scheme is matched to a Security Rule with some form of authentication, access is always denied.