Question 91
- (Exam Topic 1)
What are the three essential components of the Check Point Security Management Architecture?
Correct Answer:A
Standalone deployment - Security Gateway and the Security Management server are installed on the same machine.
Distributed deployment - Security Gateway and the Security Management server are installed on different machines.
Deployments
Basic deployments: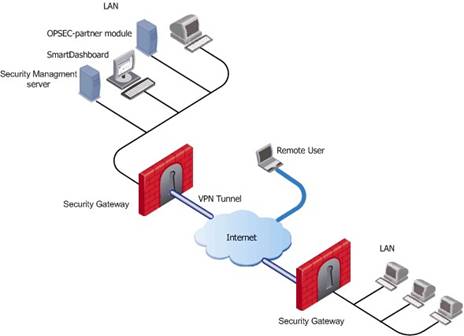
Assume an environment with gateways on different sites. Each Security Gateway connects to the Internet on one side, and to a LAN on the other.
You can create a Virtual Private Network (VPN) between the two Security Gateways, to secure all communication between them.
The Security Management server is installed in the LAN, and is protected by a Security Gateway. The Security Management server manages the Security Gateways and lets remote users connect securely to the corporate network. SmartDashboard can be installed on the Security Management server or another computer.
There can be other OPSEC-partner modules (for example, an Anti-Virus Server) to complete the network security with the Security Management server and its Security Gateways.
Question 92
- (Exam Topic 2)
What happens if the identity of a user is known?
Correct Answer:D
Question 93
- (Exam Topic 1)
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ____ .
Correct Answer:B
To enable Identity Awareness:
Log in to SmartDashboard.
From the Network Objects tree, expand the Check Point branch.
Double-click the Security Gateway on which to enable Identity Awareness.
In the Software Blades section, select Identity Awareness on the Network Security tab.
The Identity Awareness
Configuration wizard opens.
Select one or more options. These options set the methods for acquiring identities of managed and unmanaged assets.
AD Query - Lets the Security Gateway seamlessly identify Active Directory users and computers
Browser-Based Authentication - Sends users to a Web page to acquire identities from unidentified users. If Transparent Kerberos Authentication is configured, AD users may be identified transparently.
Question 94
- (Exam Topic 4)
What are the three components for Check Point Capsule?
Correct Answer:D
Question 95
- (Exam Topic 2)
Which of the following statements accurately describes the command snapshot?
Correct Answer:A
Question 96
- (Exam Topic 4)
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Correct Answer:C