Question 79
- (Exam Topic 3)
What is the command to see cluster status in cli expert mode?
Correct Answer:A
Question 80
- (Exam Topic 2)
Jack works for a managed service provider and he has been tasked to create 17 new policies for several new customers. He does not have much time. What is the BEST way to do this with R80 security management?
Correct Answer:A
Did you know: mgmt_cli can accept csv files as inputs using the --batch option.
The first row should contain the argument names and the rows below it should hold the values for these parameters.
So an equivalent solution to the powershell script could look like this:
data.csv:
mgmt_cli add host --batch data.csv -u
This can work with any type of command not just "add host" : simply replace the column names with the ones relevant to the command you need.
Question 81
- (Exam Topic 3)
What component of R80 Management is used for indexing?
Correct Answer:D
Question 82
- (Exam Topic 1)
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Correct Answer:A
The most likely reason for the logs data to stop is the low disk space on the logging device, which can be the Management Server or the Gateway Server.
Question 83
- (Exam Topic 1)
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
Correct Answer:A
vpn tu
Description Launch the TunnelUtil tool which is used to control VPN tunnels.
Usage vpn tu vpn tunnelutil Example vpn tu Output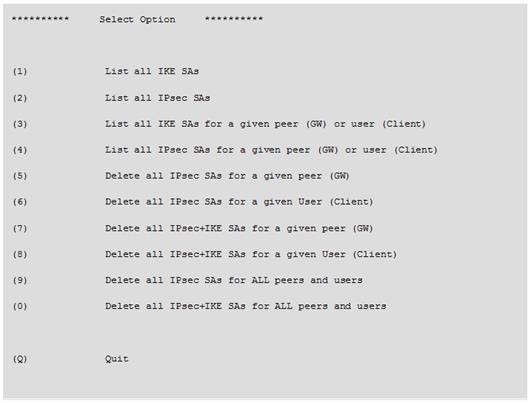
Question 84
- (Exam Topic 2)
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
Correct Answer:C