Question 31
A)
B)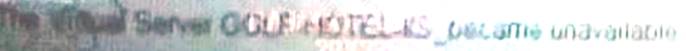
C)
Correct Answer:A
Question 32
The use of attack signature within an intrusion Detection System (IDS) is an application of which security model?
Correct Answer:C
https //www.dosarrpst.com'ddos-blog/the-difference-between-positive-s-negatto-wafi
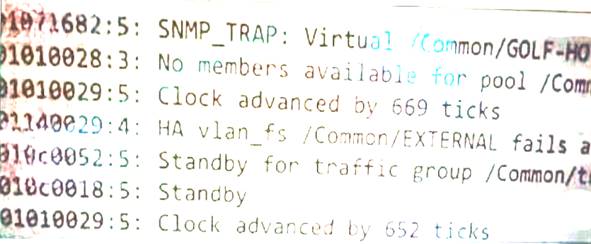
Question 33
In the Network Map a red diamond appears next to the three member servers in the Virtual Server’s pool. The nodes in the pool each show a green circle. What is the most likely reason for this scenario?
Correct Answer:D
Question 34
A company needs to use a custom value when making persistence decisions.Which F5 product provides this functionality?
Correct Answer:B
Question 35
An administrator needs to assess an LTM for potential configuration issues and required security updates. Which F5 website con automate this task?
Correct Answer:B
https://www f5.com/services/support/support-offerings/big-ip-ihealth-diagnostic-tool
Question 36
An administrator is having a connectivity issue with a server in the same network. Upon checking with the command arp -a on a Windows machine, the two outputs are taken on a 1 minute interval "hat is likely causing this issue?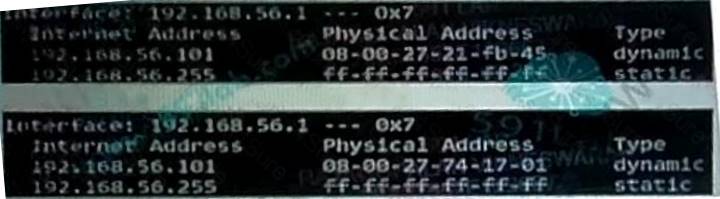
Correct Answer:D